70 410 Dumps Pdf Free Download
Cisco Certified Network Associate (200-125)
Exam Description: The Cisco Certified Network Associate (CCNA) Routing and Switching composite exam (200-125) is a 90-minute, 50–60 questions assessment that is associated with the CCNA Routing and Switching certification. This exam tests a candidate's knowledge and skills related to network fundamentals, LAN switching technologies, IPv4 and IPv6 routing technologies, WAN technologies, infrastructure services, infrastructure security, and infrastructure management.
The following topic includes all the questions likely to be included on the exam.
The questions valid until February 24, 2020
[Most recent update: February 19, 2020 | Fixed some answers ]
Table content questions:
| Section 1: Network Fundamentals | 15% | Page 1 |
| Section 2: LAN Switching Technologies | 21% | Page 2 |
| Section 3: Routing Technologies | 23% | Page 3 |
| Section 4: WAN Technologies | 10% | Page 4 |
| Section 5: Infrastructure Services | 10% | Page 5 |
| Section 6: Infrastructure Security | 11% | Page 6 |
| Section 7: Infrastructure Management | 10% | Page 7 |
| Section 8: New Questions | updating.. | Page 8 |
Section I: Network Fundamentals
I.1. In which two formats can the IPv6 address fd15:0db8:0000:0000:0700:0003:400F:572B be written? (Choose two.)
- fd15:0db8:0000:0000:700:3:400F:527B
- fd15:0db8::7:3:4F:527B
- fd15::db8::700:3:400F:527B
- fd15:db8::700:3:400F:572B
- fd15:db8:0::700:3:4F:527B
Show (Hide) Explanation/Reference
In this case we use two rules:
+ Leading zeros in a field are optional
+ Successive fields of 0 are represented as ::, but only once in an address
If you are not sure about IPV6, please read our IPv6 tutorial.
I.2. What are three characteristics of the TCP protocol? (Choose three.)
- It uses a single SYN-ACK message to establish a connection.
- The connection is established before data is transmitted.
- It ensures that all data is transmitted and received by the remote device.
- It supports significantly higher transmission speeds than UDP.
- It requires applications to determine when data packets must be retransmitted.
- It uses separate SYN and ACK messages to establish a connection.
Show (Hide) Explanation/Reference
Note: Answer F is not correct because TCP does not require applications to determine the retranmission. TCP itself will determine if the data packets should be retransmitted or not.
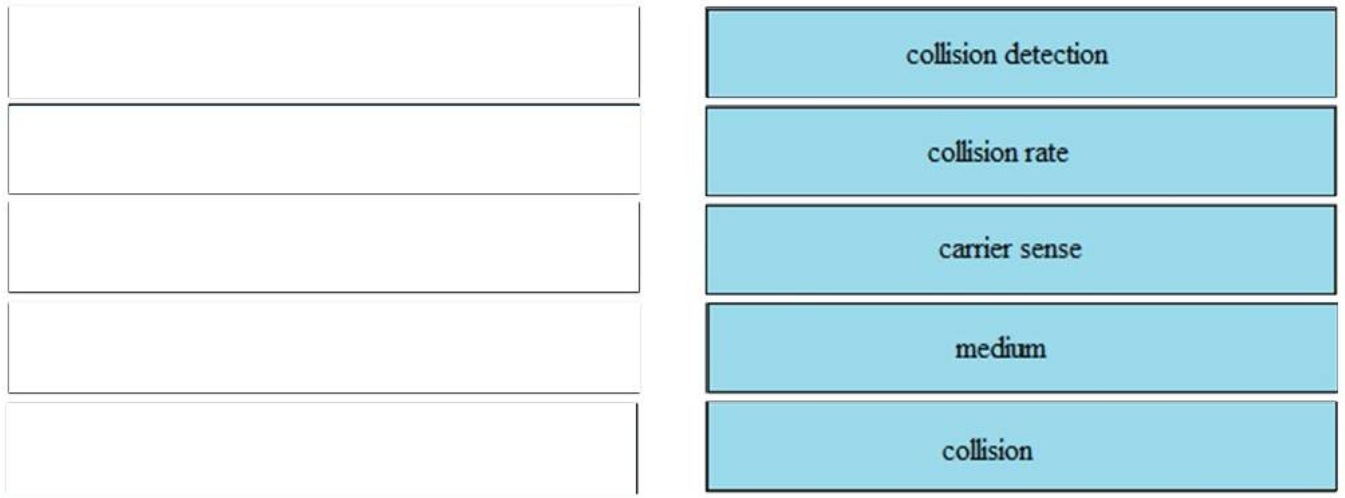
I.3. DRAG DROP. Drag and drop the Ethernet terms from the left onto the correct descriptions on the right.
Select and Place:
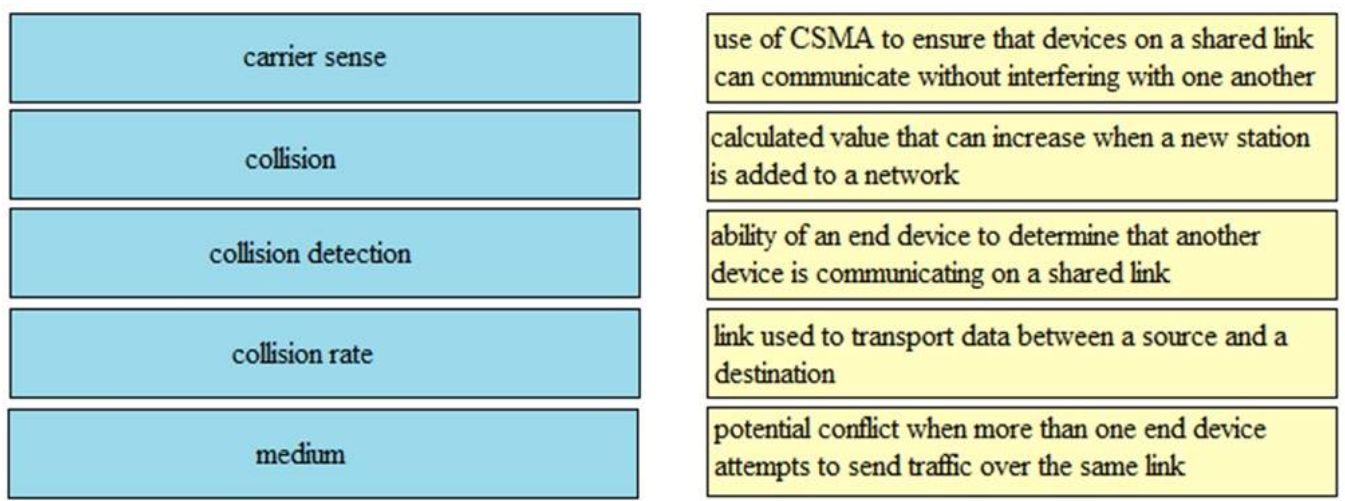
Correct Answer:
I.4. Refer to the exhibit
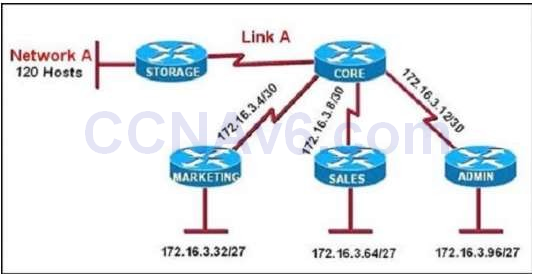
All of the routers in the network are configured with the ip subnet-zero command. Which network addresses should be used for Link A and Network A? (Choose two.)
- Link A 172.16.3.0/30
- Link A 172.16.3.112/30
- Network A 172.16.3.48/26
- Network A 172.16.3.128/25
- Link A 172.16.3.40/30
- Network A 172.16.3.192/26
Show (Hide) Explanation/Reference
Network A needs 120 hosts < 128 = 27 -> Need a subnet mask of 7 bit 0s -> "/25″.
Because the ip subnet-zero command is used, network 172.16.3.0/30 can be used.
Answer E "Link A – 172.16.3.40/30″ is not correct because this subnet belongs to MARKETING subnet (172.16.3.32/27).
Answer F "Link A – 172.16.3.112/30″ is not correct because this subnet belongs to ADMIN subnet (172.16.3.96/27).
I.5. Which type of device can be replaced by the use of subinterfaces for VLAN routing?
- Layer 2 bridge
- Layer 2 switch
- Layer 3 switch
- router
I.6. What are two benefits of private IPv4 IP addresses? (Choose two.)
- They are routed the same as public IP addresses.
- They are less costly than public IP addresses.
- They can be assigned to devices without Internet connections.
- They eliminate the necessity for NAT policies.
- They eliminate duplicate IP conflicts.
Show (Hide) Explanation/Reference
Usually using private IPv4 addresses in a organization is free so surely they are less costly than public IP addresses which you have to buy -> B is correct.
Also we can use private IPv4 addresses to devices that do not need to connect to the Internet because Internet requires public IPv4 addresses -> C is correct.
Answer D is not correct as we still need to use NAT policies to limit which private IPv4 addresses in our company can access our resources.
I.7. Which two server types are used to support DNS lookup? (Choose two.)
- web server
- ESX host
- authoritative name server
- file transfer server
- name resolver
I.8. Which three statements about IPv6 prefixes are true? (Choose three.)
- FEC0::/10 is used for IPv6 broadcast.
- FC00::/7 is used in private networks.
- FE80::/8 is used for link-local unicast.
- FE80::/10 is used for link-local unicast.
- 2001::1/127 is used for loopback addresses.
- FF00::/8 is used for IPv6 multicast.
Show (Hide) Explanation/Reference
Below is the list of common kinds of IPv6 addresses:
| Loopback address | ::1 |
| Link-local address | FE80::/10 |
| Site-local address | FEC0::/10 (but it is deprecated and replaced with FC00::/7 for used in private networks) |
| Global address | 2000::/3 |
| Multicast address | FF00::/8 |
I.9. Refer to the exhibit
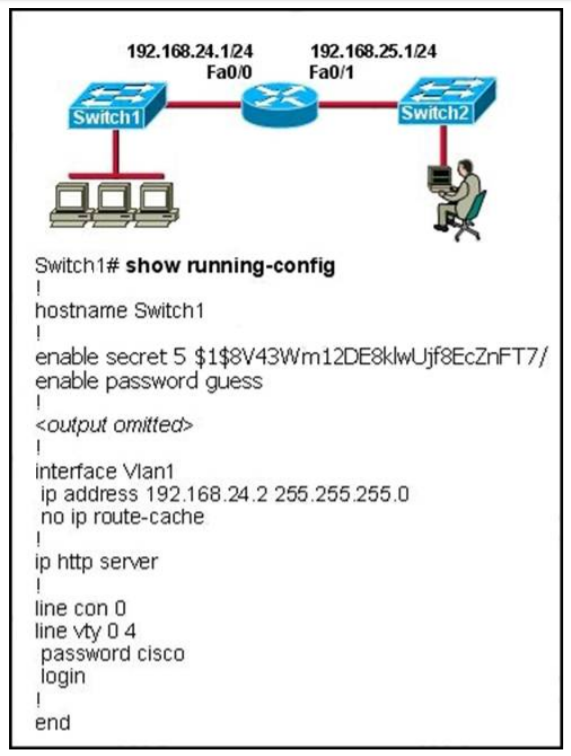
The network administrator cannot connect to Switch 1 over a Telnet session, although the hosts attached to Switch1 can ping the interface Fa0/0 of the router. Given the information in the graphic and assuming that the router and Switch2 are configured properly, which of the following commands should be issued on Switch1 to correct this problem?
- Switch1(config)# ip default-gateway 192.168.24.1
- Switch1(config)# interface fa0/1Switch1(config-if)# switchport mode trunk
- Switch1(config)# line con0Switch1(config-line)# password ciscoSwitch1(config-line)# login
- Switch1(config)# interface fa0/1Switch1(config-if)# ip address 192.168.24.3 255.255.255.0
- Switch1(config)# interface fa0/1Switch1(config-if)# duplex fullSwitch1(confiq-if)# speed 100
I.10. Which two statements about IPv6 and routing protocols are true? (Choose two.)
- Link-local addresses are used to form routing adjacencies.
- OSPFv3 was developed to support IPv6 routing.
- EIGRP, OSPF, and BGP are the only routing protocols that support IPv6.
- Loopback addresses are used to form routing adjacencies.
- EIGRPv3 was developed to support IPv6 routing.
Show (Hide) Explanation/Reference
Link-local addresses only used for communications within the local subnetwork (automatic address configuration, neighbor discovery, router discovery, and by many routing protocols). It is only valid on the current subnet. It is usually created dynamically using a link-local prefix of FE80::/10 and a 64-bit interface identifier (based on 48-bit MAC address).
I.11. What will happen if a private IP address is assigned to a public interface connected to an ISP?
- Addresses in a private range will be not be routed on the Internet backbone.
- Only the ISP router will have the capability to access the public network.
- The NAT process will be used to translate this address to a valid IP address.
- A conflict of IP addresses happens, because other public routers can use the same range.
I.12. DRAG DROP. Refer to the exhibit.
Select and Place:
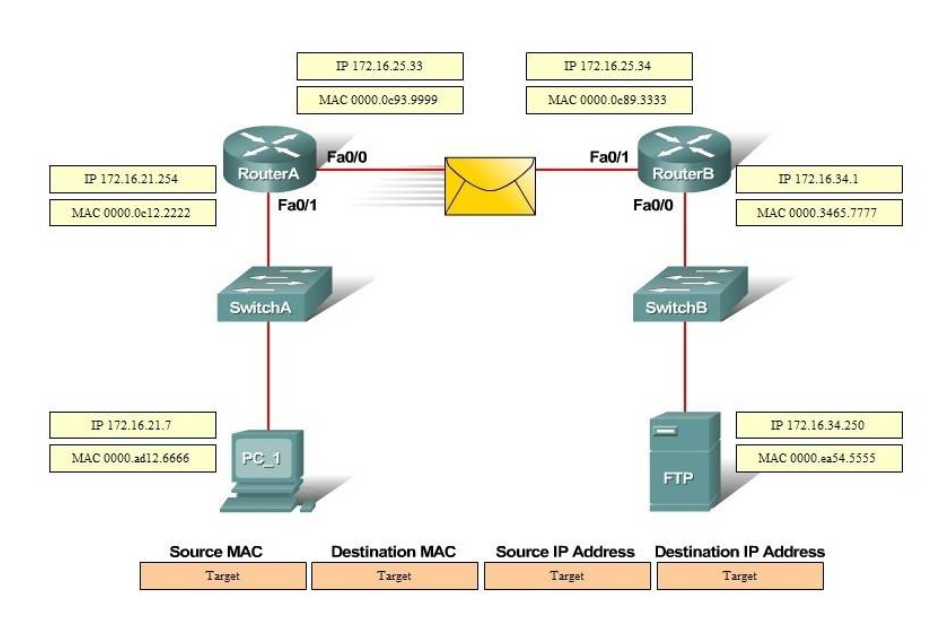
Correct Answer:
I.13. Which two statements about wireless LAN controllers are true? (Choose two.)
- They can simplify the management and deployment of wireless LANs.
- They rely on external firewalls for WLAN security.
- They are best suited to smaller wireless networks.
- They must be configured through a GUI over HTTP or HTTPS.
- They can manage mobility policies at a systemwide level.
Show (Hide) Explanation/Reference
Cisco Wireless is designed to provide 802.11 wireless networking solutions for enterprises and service providers. Cisco Wirelesssimplifies deploying and managing large-scale wireless LANs and enables a unique best-in-class security infrastructure. The operating system manages all data client, communications, and system administration functions, performs radio resource management (RRM) functions,manages system-wide mobility policies using the operating system security solution, and coordinates all security functions using the operating system security framework.
Reference: http://www.cisco.com/c/en/us/td/docs/wireless/controller/8-2/config-guide/b_cg82/b_cg82_chapter_01.html
I.14. Which step in the router boot process searches for an IOS image to load into the router?
- bootstrap
- POST
- mini-IOS
- ROMMON mode
Show (Hide) Explanation/Reference
The following details the router boot process:
1. The router is powered on.
2. The router first runs Power-On Self Test (POST)
3. The bootstrap checks the Configuration Register value to specify where to load the IOS. By default (the default value of Configuration Register is 2102, in hexadecimal), the router first looks for "boot system" commands in startup-config file. If it finds these commands, it will run boot system commands in order they appear in startup-config to locate the IOS. If not, the IOS image is loaded from Flash . If the IOS is not found in Flash, the bootstrap can try to load the IOS from TFTP server or from ROM (mini-IOS).
4. After the IOS is found, it is loaded into RAM.
5. The IOS attempts to load the configuration file (startup-config) from NVRAM to RAM. If the startup-config is not found in NVRAM, the IOS attempts to load a configuration file from TFTP. If no TFTP server responds, the router enters Setup Mode (Initial Configuration Mode).
For more information about booting process please read our Cisco Router Boot Sequence tutorial.
I.15. Which protocol advertises a virtual IP address to facilitate transparent failover of a Cisco routing device?
- FHRP
- DHCP
- RSMLT
- ESRP
Show (Hide) Explanation/Reference
First Hop Redundancy Protocol (FHRP) is a protocol that enables two or more devices to work together in a group, sharing a single IP address, the virtual IP address. One router is elected to handle all requests sent to the virtual IP address. With HSRP, this is the active router. An HSRP group has one active router and at least one standby router.
I.16. Refer to exhibit. Which command can you enter to verify link speed and duplex setting on the interface?
R1(config)#interface gigabitEthernet0/1 R1(config-if)#ip address 192.168.1.1. 255.255.255.0 R1(config-if)#speed 100 R1(config-if)#duplex full
- router#show ip protocols
- router#show startup-config
- router#show line
- router#show interface gig 0/1
Show (Hide) Explanation/Reference
The "show interfaces …" command gives us information about speed and duplex mode of the interface. In the output below, the link speed is 100Mbps and it is working in Full-duplex mode.
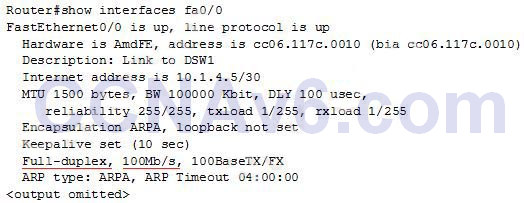
I.17. Which utility can you use to determine whether a switch can send echo requests and replies?
- ping
- traceroute
- ssh
- telnet
Show (Hide) Explanation/Reference
"ping" command is used to send echo requests and receive echo replies.
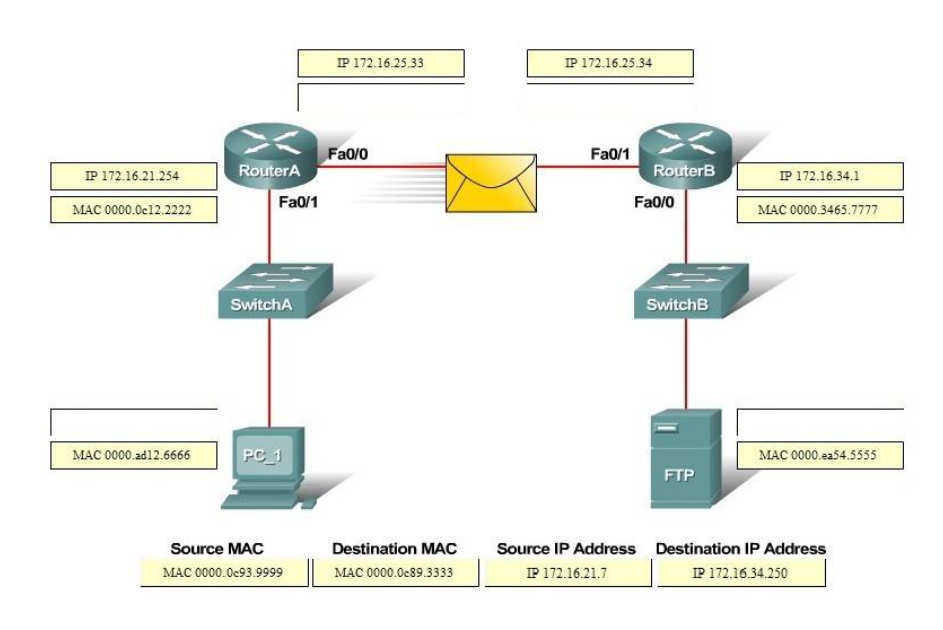
I.18. If computer A is sending traffic to computer B, which option is the source IP address when a packet leaves R1 on interface F0/1?
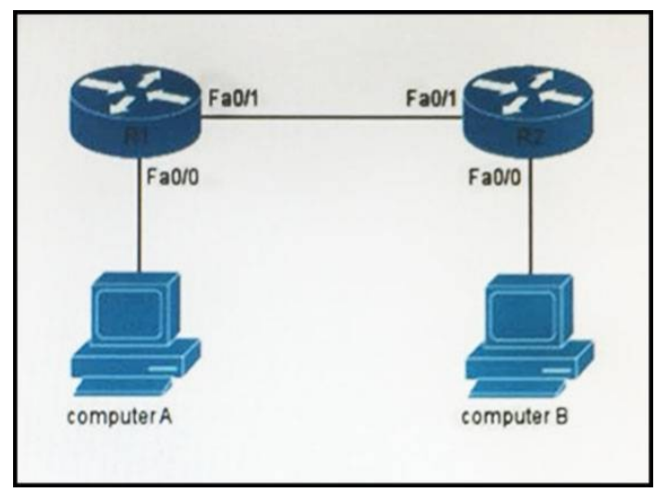
- IP address of the R2 interface F0/1
- Ip address of computer B
- Ip address of R1 interface F0/1
- Ip address of Computer A
Show (Hide) Explanation/Reference
In all the way on the path, the source and destination IP addresses never change, only the source and destination MAC address are changed on each segment.
I.19. Which functionality does split horizon provide?
- It prevents switching loops in distance-vector protocols.
- It prevents switching loops in link-state protocols.
- It prevents routing loops in distance-vector protocols.
- It prevents routing loops in link-state protocols.
I.20. Which MAC protocol sets a random timer to reattempt communication ?
- RARP
- CSMA/CA
- CSMA/CD
- IEEE 802.1x
I.21. How many host addresses are available on the network 192.168.1.0 subnet 255.255.255 240?
- 6
- 8
- 14
- 16
I.22. Which two statements about unique local IPv6 addresses are true?
- They are identical to IPv4 private addresses.
- They are defined by RFC 1884
- They use the prefix FEC0::/10
- They use the prefix FC00::/7
- They can be routed on the IPv6 global internet.
Show (Hide) Explanation/Reference
A IPv6 Unique Local Address is an IPv6 address in the block FC00::/7. It is the approximate IPv6 counterpart of the IPv4 private address. It is not routable on the global Internet.Note: In the past, Site-local addresses (FEC0::/10) are equivalent to private IP addresses in IPv4 but now they are deprecated.
I.23. If three devices are plugged into one port on a switch and two devices are plugged into a different port, how many collision domains are on the switch?
- 2
- 4
- 5
- 6
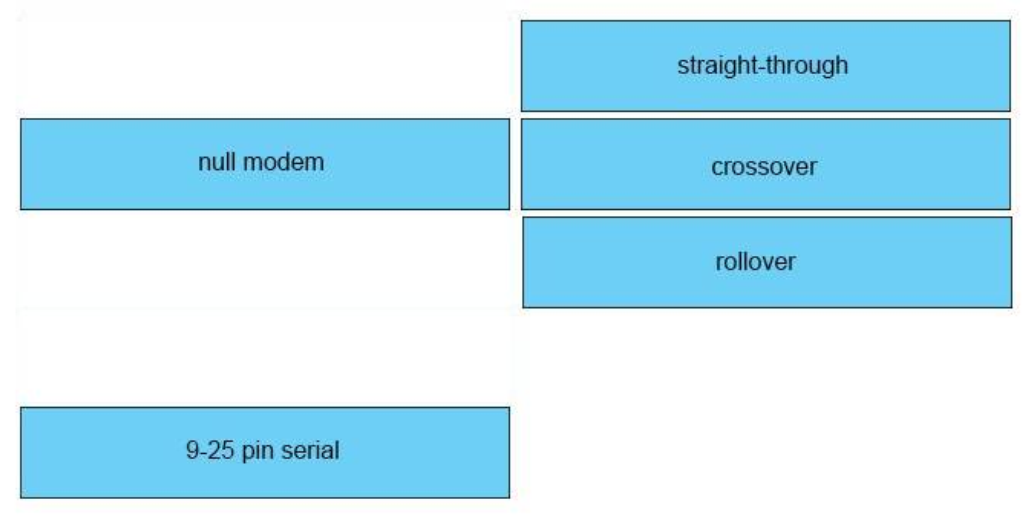
I.24. DRAG DROP. Drag the cable type on the left to the purpose for which is the best suited on the right. Not all options are used.
Select and Place:
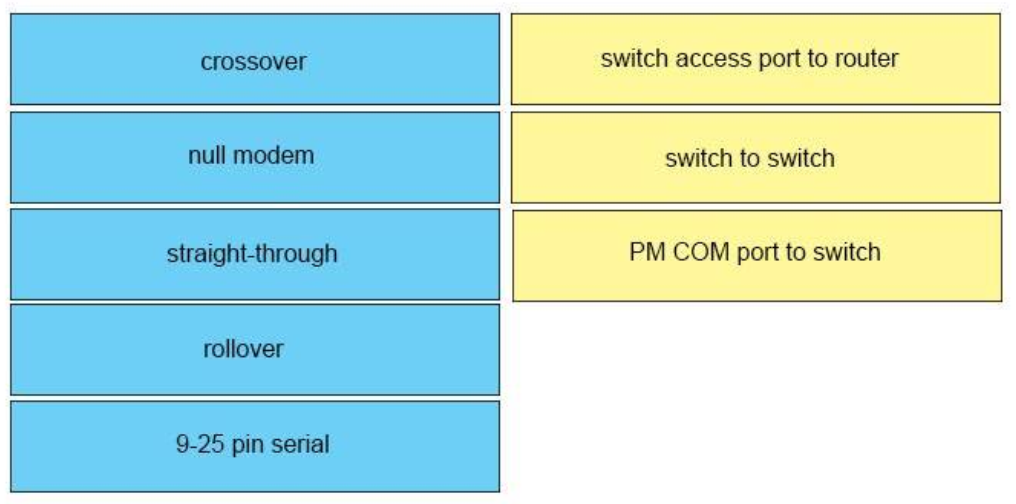
Correct Answer:
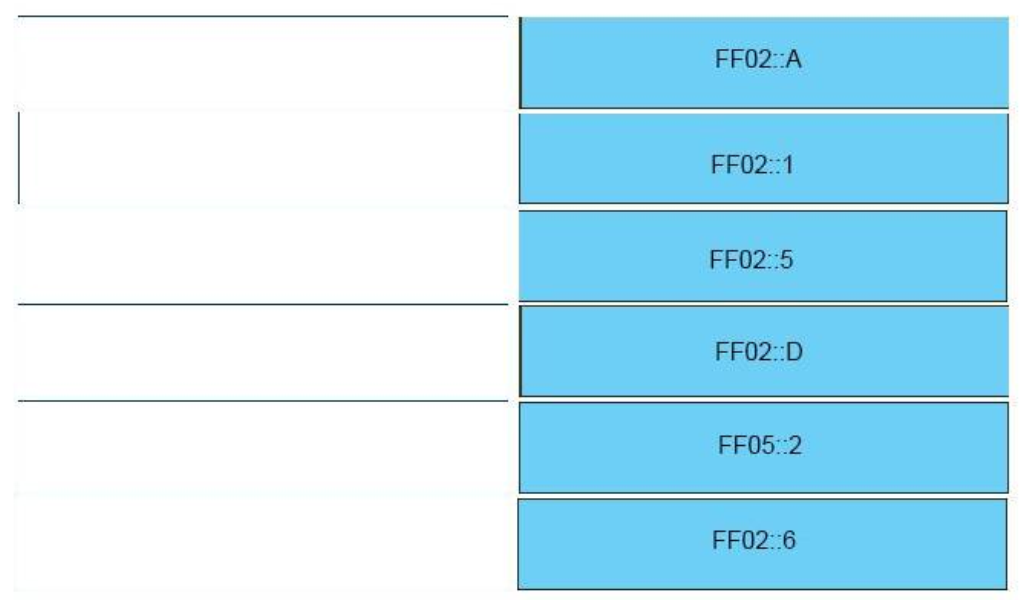
I.25. DRAG DROP. Drag the IPv6 multicast address type on the left to their purpose on the right..
Select and Place:
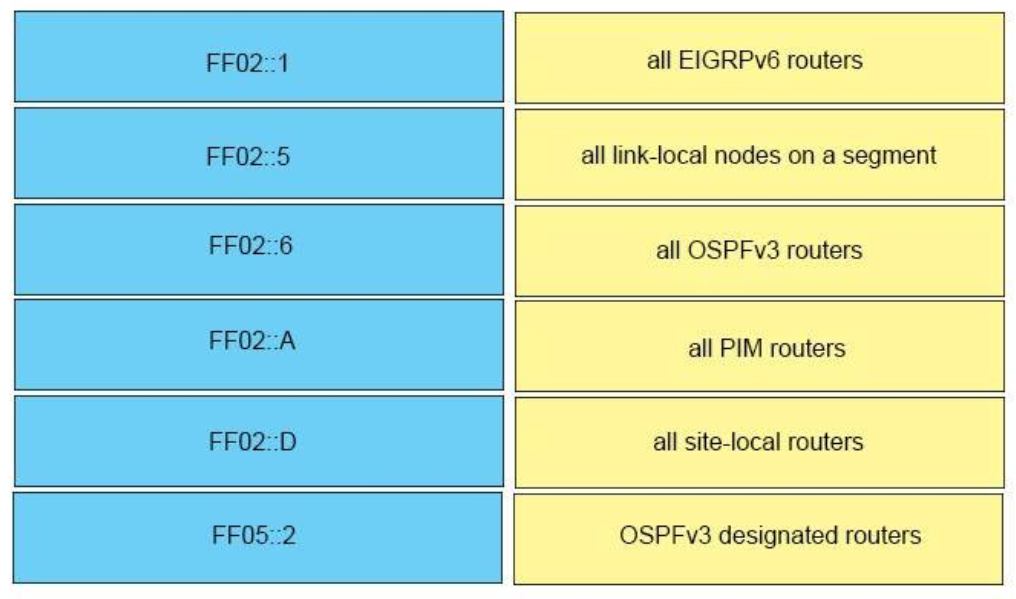
Correct Answer:
I.26. How does a router handle an incoming packet whose destination network is missing from the routing table?
- it broadcast the packet to each interface on the router
- it discards the packet
- it broadcasts the packet to each network on the router
- it routes the packet to the default route
Show (Hide) Explanation/Reference
Change from "it discards the packet" to "it routes the packet to the default route" because there is new question Which definition of default route is true? with answer "A route used when a destination route is missing."
I.27. Which two statements about Ethernet standards are true?(choose two)
- Ethernet is defined by IEEE standard 802.2
- Ethernet is defined by IEEE standard 802.3
- Ethernet 10BASE-T dose not support full-duplex.
- When an Ethernet network uses CSMA/CD ,it terminates transmission as soon as collision occurs
- When an Ethernet network uses CSMA/CA ,it terminates transmission as soon as collision occurs
I.28. Which command enables IPv6 forwarding on a Cisco router?
- ipv6 local
- ipv6 host
- ipv6 unicast-routing
- ipv6 neighbor
Show (Hide) Explanation/Reference
An example of configuring RIPng (similar to RIPv2 but is used for IPv6) is shown below:
Router(config)#ipv6 unicast-routing (Enables the forwarding of IPv6 unicast datagrams globally on the router)
Router(config)#interface fa0/0
Router(config-if)#ipv6 rip 9tut enable (9tut is the process name of this RIPng)
I.29. Refer to the exhibit. If R1 receives a packet destined to 172.16.1.1, to which IP address does it send the packet?
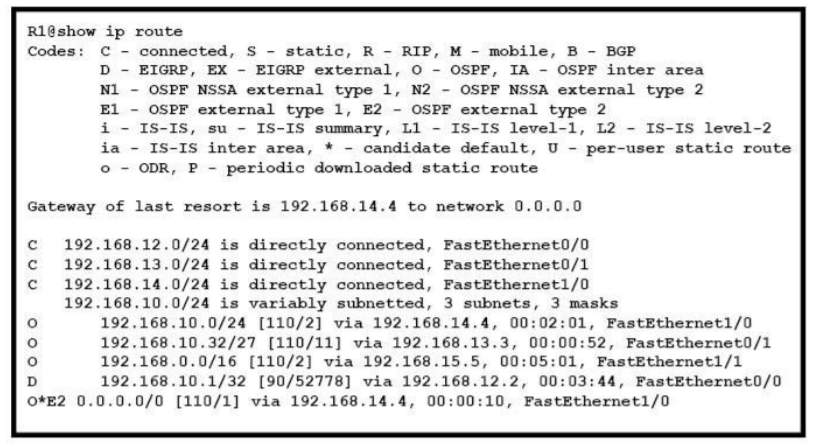
- 192.168.14.4
- 192.168.12.2
- 192.168.13.3
- 192.168.15.5
Show (Hide) Explanation/Reference
It can't find the address 172.16.1.1 so it will be directed to the Gate of last resort 192.168.14.4
I.30. What is known as "one-to-nearest" addressing in IPv6?
- global unicast
- anycast
- multicast
- unspecified address
I.31. When a router is unable to find a known route in the routing table, how does it handle the packet?
- It discards the packet
- It sends the packet over the route with the best metric
- It sends the packet to the next hop address
- It sends the packet to the gateway of last resort
Show (Hide) Explanation/Reference
In fact this question is not clear. If we understand that "router is unable to find a known route in the routing table" and there is no default route in the routing table then the router will surely discard the packet -> A is correct. But we are not sure if there is a default route or not so let learn more about gateway of last resort.
A Gateway of Last Resort is a route used by the router when no other known route exists to send the IP packet. For CCNA level, when ip routing feature is enabled, a gateway of last resort is usually created by:
+ The "ip default-network" command (but dynamic routing protocols have different behaviors). But in general, the "ip default-network" cannot set the gateway of last resort without a known route in the routing table.
+ Creating a static route to network 0.0.0.0 0.0.0.0 is another way to set the gateway of last resort on a router. This is the reason why this question is not clear as it does not tell us if a default route exists or not.
Maybe in this question a default route does not exist. Otherwise the author would notice and indicate it in the question.
For more information about Gateway of Last Resort, please read:
http://www.cisco.com/c/en/us/support/docs/ip/routing-information-protocol-rip/16448-default.html
I.32. If router R1 knows a static route to a destination network and then learns about the same destination network through a dynamic routing protocol, how does R1 respond?
- It refuses to advertise the dynamic route to other neighbors
- It sends a withdrawal signal to the neighboring router
- It disables the routing protocol
- It prefers the static route
Show (Hide) Explanation/Reference
By default the administrative distance of a static route is 1, meaning it will be preferred over all dynamic routing protocols. If you want to have the dynamic routing protocol used and have the static route be used only as a backup, you need to increase the AD of the static route so that it is higher than the dynamic routing protocol.
I.33. Which option is the correct CIDR notation for 192.168.0.0 subnet 255.255.255.252?
- /29
- /30
- /31
- /32
I.34. Which six-byte field in a basic Ethernet frame must be an individual address?
- SOF
- FCS
- DA
- SA
Show (Hide) Explanation/Reference
The picture below shows the fields in IEEE 802.1Q frame.
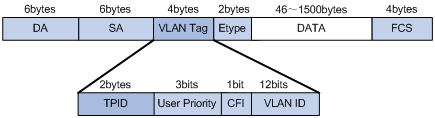
The SA field is the source address field. The field should be set to the MAC address of the switch port that transmits the frame. It is a 48-bit value (6 bytes). The receiving device may ignore the SA field of the frame.
In fact there is another correct answer for this question: DA (Destination Address) which also consists of 6 bytes. Maybe there is a mistake or typo in this question.
Which statement a
I.35. If a router has four interfaces and each interface is connected to four switches, how many broadcast domains are present on the router?
- 1
- 2
- 4
- 8
Show (Hide) Explanation/Reference
Remember that only route interface can separate broadcast domain (while switch interface separate collision domain) so the broadcast domains are equal to the number of router interfaces, which is four in this case.
I.36. Refer to the exhibit. What is the most appropriate summarization for these routes?
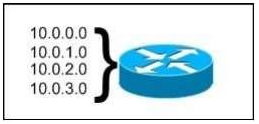
- 10.0.0.0 /21
- 10.0.0.0 /22
- 10.0.0.0 /23
- 10.0.0.0 /24
Show (Hide) Explanation/Reference
The 10.0.0.0/22 subnet mask will include the 10.0.0.0, 10.0.1.0, 10.0.2.0, and 10.0.3.0 networks, and only those four networks.
I.37. What 8-bit field exists in IP packet for QoS?
- Tos Field
- DSCP
- IP Precedence
- Cos
- -ANOTHER OPTION-
Show (Hide) Explanation/Reference
The IP datagram header contains an 8-bit field called ToS (Type of Service). The field has been part of the IP header since the beginning, but it was rarely used until the recent introduction of Differentiated Services (Diff-Serv).
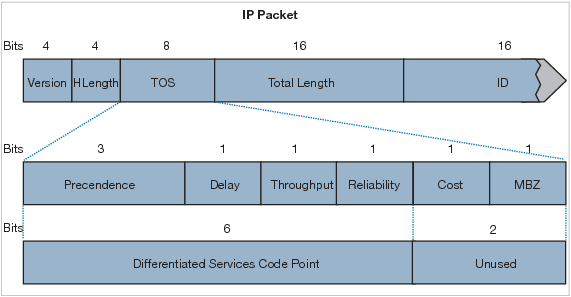
Note:
+ CoS does not exists in an IP header. It appears in the header of a 802.1Q frame only. CoS is used for QoS on a trunk link.
+ DSCP uses the first 6 bits of the TOS field.
I.38. What feature uses a random time to re-send a frame?
- CSMA/CA
- -ANOTHER OPTION-
- -ANOTHER OPTION-
- CSMA/CD
I.39. Two hosts are attached to a switch with the default configuration. Which statement about the configuration is true?
- IP routing must be enabled to allow the two hosts to communicate.
- The two hosts are in the same broadcast domain.
- The switch must be configured with a VLAN to allow the two hosts to communicate.
- Port security prevents the hosts from connecting to the switch.
Show (Hide) Explanation/Reference
All ports on a Layer 2 switch are in the same broadcast domain. Only router ports separate broadcast domains.
I.40. If a router has 3 hosts connected in one port and two other hosts connected in another port, how may broadcast domains are present on the router?
- 5
- 2
- 3
- 4
I.41. What are three parts of an IPv6 global unicast address? (Choose three.)
- an interface ID that is used to identify the local host on the network.
- an interface ID that is used to identify the local network for a particular host.
- a subnet ID that is used to identify networks inside of the local enterprise site
- a global routing prefix that is used to identify the network portion of the address that has been provided by an ISP
- a global routing prefix that is used to identify the portion of the network address provided by a local administrator
Show (Hide) Explanation/Reference
IPv6 includes two different unicast address assignments:
+ Global unicast address
+ Link-local address
The global unicast address is globally unique in the Internet. The example IPv6 address that is shown below is a global unicast address.
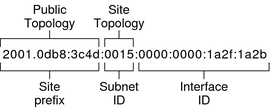
+Site prefix (global routing prefix): defines the public topology of your network to a router. You obtain the site prefix for your enterprise from an ISP or Regional Internet Registry (RIR).
+Site Topology and Subnet ID: the subnet ID defines an administrative subnet of the network and is up to 16 bits in length. You assign a subnet ID as part of IPv6 network configuration. The subnet prefix defines the site topology to a router by specifying the specific link to which the subnet has been assigned
+Interface ID: identifies an interface of a particular node. An interface ID must be unique within the subnet.
Reference: https://docs.oracle.com/cd/E23823_01/html/816-4554/ipv6-overview-10.html
I.42. You have been asked to come up with a subnet mask that will allow all three web servers to be on the same network while providing the maximum number of subnets. Which network address and subnet mask meet this requirement?
- 192.168.252.0 255.255.255.252
- 192.168.252.8 255.255.255.248
- 192.168.252.8 255.255.255.252
- 192.168.252.16 255.255.255.240
- 192.168.252.16 255.255.255.252
I.43. DRAG DROP. Drag and drop the IPv6 IP addresses from the left onto the correct IPv6 address types on the right.
Select and Place:
Correct Answer:
I.44. What is the correct routing match to reach 172.16.1.5/32?
- 172.16.1.0/26
- 172.16.1.0/25
- 172.16.1.0/24
- the default route
Show (Hide) Explanation/Reference
Although all above answers are correct but 172.16.1.0/26 is the best choice as it is the most specific prefix-match one.
I.45. Which layer in the OSI reference model is responsible for determining the availability of the receiving program and checking to see if enough resources exist for that communication?
- transport
- network
- presentation
- session
- application
I.46. What are the address that will show at the show ip route if we configure the above statements? (Choose Three.)

- 10.0.0.0
- 10.4.3.0
- 172.15.4.0
- 172.15.0.0
- 192.168.4.0
- 192.168.0.0
Show (Hide) Explanation/Reference
With auto-summary feature is turned on, EIGRP will summary these networks to their classful networks automatically. For example:
+ 172.15.4.0 belongs to class B so it will be summarized to 172.15.0.0
+ 10.4.3.0 belongs to class A so it will be summarized to 10.0.0.0
+ 192.168.4.0 belongs to class C so it will be summarized to 192.168.4.0 (same)
I.47. Which feature facilitates the tagging of frames on a specific VLAN?
- Routing
- Hairpinning
- Encapsulation
- Switching
I.48. What does split horizon prevent?
- routing loops, link state
- routing loops, distance vector
- switching loops, STP
- switching loops, VTP
Show (Hide) Explanation/Reference
Split horizon is used in distance vector routing protocols (like RIP, EIGRP) to prevent routing loops by prohibiting a router from advertising a route back to the interface from which it was learned.
I.49. Which IPV6 feature is supported in IPV4 but is not commonly used?
- unicast
- multicast
- anycast
- broadcast
Show (Hide) Explanation/Reference
Only three connection types are commonly known and used in Internet Protocol version four (IPv4) networks: unicast, multicast and broadcast. A fourth connection type, Anycast, was unknown until IPv6 made it a standard connection type. Anycast is not standardized in IPv4 but can be emulated. IPv4 Anycast addressing is a good solution to provide localization for services and servers in order to obtain robustness, redundancy and resiliency.
The basic idea of Anycast is very simple: multiple servers, which share the same IP address, host the same service. The routing infrastructure sends IP packets to the nearest server (according to the metric of the routing protocol used). The major benefits of employing Anycast in IPv4 are improved latency times, server load balancing, and improved security.
Reference: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.116.6367&rep=rep1&type=pdf
I.50. What is the binary pattern of unique ipv6 unique local address?
- 00000000
- 11111100
- 11111111
- 11111101
Show (Hide) Explanation/Reference
A IPv6 Unique Local Address is an IPv6 address in the block FC00::/7, which means that IPv6 Unique Local addresses begin with 7 bits with exact binary pattern as 1111 110 -> Answer B is correct.
Note: IPv6 Unique Local Address is the approximate IPv6 counterpart of the IPv4 private address. It is not routable on the global Internet.
I.51. Describe the best way to troubleshoot and isolate a network problem?
- Create an action plan
- Implement an action plan
- Gather facts
- others
Show (Hide) Explanation/Reference
In fact all three of the above answers are in the problem-solving process but "gather facts" is at Step 2 while "Create an action plan" and "Implement an action plan" is at step 4 & 5 of this link http://www.cisco.com/en/US/docs/internetworking/troubleshooting/guide/tr1901.html
Step 2 Gather the facts that you need to help isolate possible causes.
Ask questions of affected users, network administrators, managers, and other key people. Collect information from sources such as network management systems, protocol analyzer traces, output from router diagnostic commands, or software release notes.
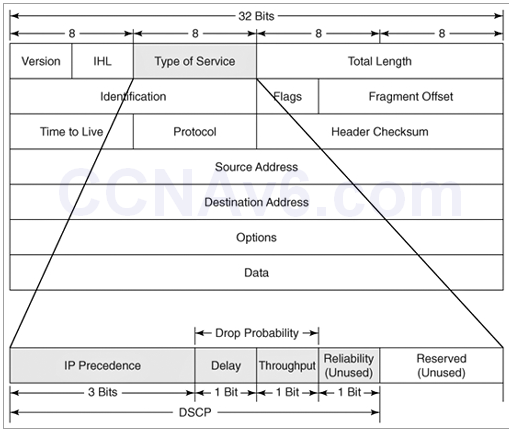
I.52. In which byte of an IP packet can traffic be marked?
- the QoS byte
- the CoS byte
- the ToS byte
- the DSCP byte
Show (Hide) Explanation/Reference
I.53. What are two benefits of Private IPv4 Addresses? (Choose two.)
- they can be implemented without requiring admin to coordinate with IANA
- they are managed by IANA
- increase the flexibility of network design
- provide network isloation from the internet
- they are routable over internet
Show (Hide) Explanation/Reference
http://smallbusiness.chron.com/advantages-disadvantages-using-private-ip-address-space-46424.html
I.54. How many bits represent network id in a IPv6 address?
- 32
- 48
- 64
- 128
Show (Hide) Explanation/Reference
Each ISP receives a /32 and provides a /48 for each site-> every ISP can provide 2(48-32) = 65,536 site addresses (note: each network organized by a single entity is often called a site).
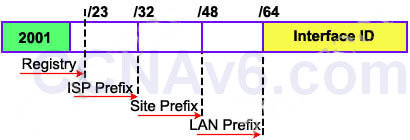
Each site provides /64 for each LAN -> each site can provide 2(64-48) = 65,536 LAN addresses for use in their private networks.
So each LAN can provide 264 interface addresses for hosts.
-> Global routing information is identified within the first 64-bit prefix.
Now let's see an example of IPv6 prefix: 2001:0A3C:5437:ABCD::/64:
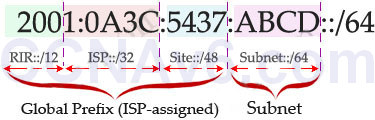
In this example, the RIR has been assigned a 12-bit prefix. The ISP has been assigned a 32-bit prefix and the site is assigned a 48-bit site ID. The next 16-bit is the subnet field and it can allow 216, or 65536 subnets. This number is redundant for largest corporations on the world!
The 64-bit left (which is not shown the above example) is the Interface ID or host part and it is much more bigger: 64 bits or 264 hosts per subnet! For example, from the prefix 2001:0A3C:5437:ABCD::/64 an administrator can assign an IPv6 address 2001:0A3C:5437:ABCD:218:34EF:AD34:98D to a host.
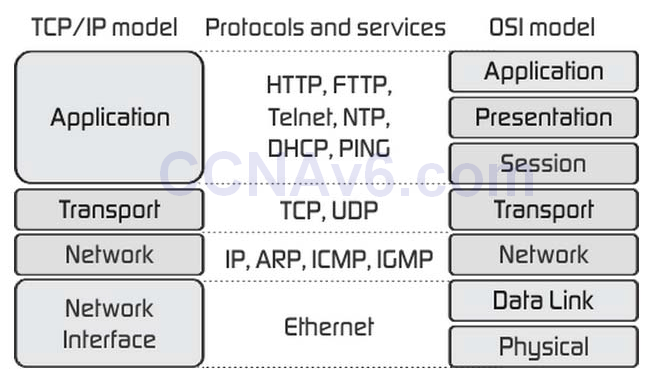
I.55. What layer of the OSI Model is included in TCP/IP Model's INTERNET layer?
- Application
- Session
- Data Link
- Presentation
- Network
Show (Hide) Explanation/Reference
The Internet Layer in TCP/IP Model is equivalent to the Network Layer of the OSI Model.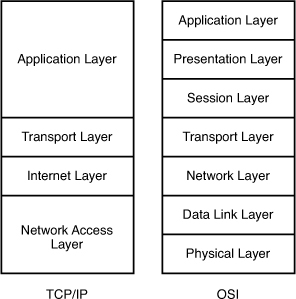
I.56. Which two features can dynamically assign IPv6 addresses? (Choose two.)
- IPv6 stateless autoconfiguration
- DHCP
- NHRP
- IPv6 stateful autoconfiguration
- ISATAP tunneling
Show (Hide) Explanation/Reference
Answer "DHCP" is not correct because DHCP can only assign IPv4 address. To assign IPv6 address, DHCPv6 should be used instead.
Answer "NHRP" is not correct because it is a protocol used in DMVPN.
Answer "ISATAP tunneling" is not correct because it is an IPv6 transition mechanism to transmit IPv6 packets between dual-stack nodes on top of an IPv4 network.
The two types of autoconfiguration are "stateless" and "stateful."
Stateful autoconfiguration is the IPv6 equivalent of DHCP. A new protocol, called DHCPv6 (and based closely on DHCP), is used to pass out addressing and service information in the same way that DHCP is used in IPv4. This is called "stateful" because the DHCP server and the client must both maintain state information to keep addresses from conflicting, to handle leases, and to renew addresses over time -> Answer "IPv6 stateful autoconfiguration" is correct.
Stateless Autoconfiguration allows an interface to automatically "lease" an IPv6 address and does not require the establishment of an server to delve out address space. Stateless autoconfiguration allows a host to propose an address which will probably be unique (based on the network prefix and its Ethernet MAC address) and propose its use on the network. Because no server has to approve the use of the address, or pass it out, stateless autoconfiguration is simpler. This is the default mode of operation for most IPv6 systems, including servers. So answer "IPv6 stateless autoconfiguration" is correct too.
I.57. How many usable host are there per subnet if you have the address of 192.168.10.0 with a subnet mask of 255.255.255.240?
- 4
- 8
- 16
- 14
Show (Hide) Explanation/Reference
From the subnet mask of 255.255.255.240 (/28) we learn there are 24 – 2 = 14 hosts per subnet.
I.58. Which type of cable must you use to connect two devices with MDI interfaces?
- rolled
- crossover
- crossed
- straight through
Show (Hide) Explanation/Reference
Use an Ethernet straight-through cable to connect an medium dependent interface (MDI) to an MDI-X port. Use a <strong>cross-over cable</strong> to connect an MDI to an MDI port, or an MDI-X to an MDI-X port.
Reference: <a href="https://www.cisco.com/c/en/us/td/docs/security/asa/hw/maintenance/5505guide/ASA5505HIG/pinouts.html" target="_blank" rel="noopener noreferrer">https://www.cisco.com/c/en/us/td/docs/security/asa/hw/maintenance/5505guide/ASA5505HIG/pinouts.html</a>
Note: MDI/MDIX is a type of Ethernet port connection using twisted pair cabling.
I.59. Which type of IPv6 address also exists in IPv4 but is barely used?
- unicast
- multicast
- anycast
- broadcast
I.60. At which layer of the OSI model dose PPP perform?
- Layer 2
- Layer 3
- Layer 4
- Layer 5
- Layer 1
I.61. Which IPv6 header field is equivalent to the TTL?
- Scan Timer.
- TTD.
- Flow Label.
- Hop Limit.
- Hop Count.
Show (Hide) Explanation/Reference
This field is same as Time To Live (TTL) in IPv4, which is used to stop packet to loop in the network infinitely. The value of Hop Limit field is decremented by 1 when it passes a Layer 3 device (like a router). When this field reaches 0 the packet is dropped.
I.62. Which IP configuration does the CIDR notation 192.168.1.1/25 refer?
- 192.168.1.1 255.255.255.64
- 192.168.1.1 255.255.255.1
- 192.168.1.1 255.255.255.32
- 192.168.1.1 255.255.255.256
- 192.168.1.1 255.255.255.128
Show (Hide) Explanation/Reference
"/25" means 1111 1111.1111 1111.1000 0000 in binary or 255.255.255.128 in decimal.
I.63. Which option is the correct CIDR notation for 192.168.0.0 subnet 255.255.255.252?
- 30
- 31
- 32
- 33
I.64. Which two functions can be performed by a local DNS server? (Choose two.)
- assigning IP addresses to local clients
- copying updated IOS images to Cisco switches
- resolving names locally
- forwarding name resolution requests to an external DNS server
- transferring split horizon traffic between zones
I.65. Refer to the exhibit. Which three statements correctly describe Network Device A? (Choose three.)
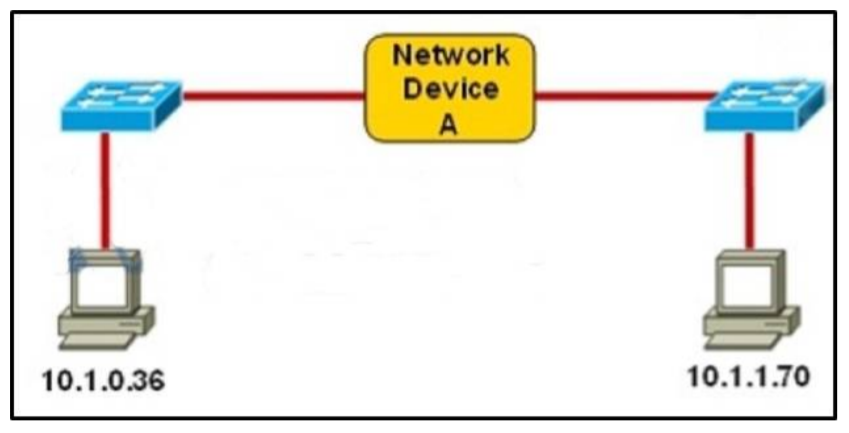
- With a network wide mask of 255.255.255.128, each interface does not require an IP address.
- With a network wide mask of 255.255.255.128, each interface does require an IP address on a unique IP subnet.
- With a network wide mask of 255.255.255.0, must be a Layer 2 device for the PCs to communicate with each other.
- With a network wide mask of 255.255.255.0, must be a Layer 3 device for the PCs to communicate with each other.
- With a network wide mask of 255.255.254.0, each interface does not require an IP address.
Show (Hide) Explanation/Reference
The principle here is if the subnet mask makes two IP addresses 10.1.0.36 and 10.1.1.70 in the same subnet then the Network device A does not need to have IP addresses on its interfaces (and we don't need a Layer 3 device here).
A quick way to find out the correct answers is notice that all 255.255.255.x subnet masks will separate these two IP addresses into two separate subnets so we need a Layer 3 device here and each interface must require an IP address on a unique IP subnet -> A, C are not correct while B, D are correct.
With 255.255.254.0 subnet mask, the increment here is 2 in the third octet -> the first subnet is from 10.1.0.0 to 10.1.1.255, in which two above IP addresses belong to -> each interface of Network device A does not require an IP address -> E is correct.
I.66. Which two tasks does a router perform when it receives a packet that is being forwarded from one network to another? (Choose two.)
- It removes the Layer 2 frame header and trailer
- It encapsulates the Layer 2 packet
- It removes the Layer 3 frame header and trailer
- It examines the routing table for the best path to the destination IP address of the packet
- It examines the MAC address table for the forwarding interface
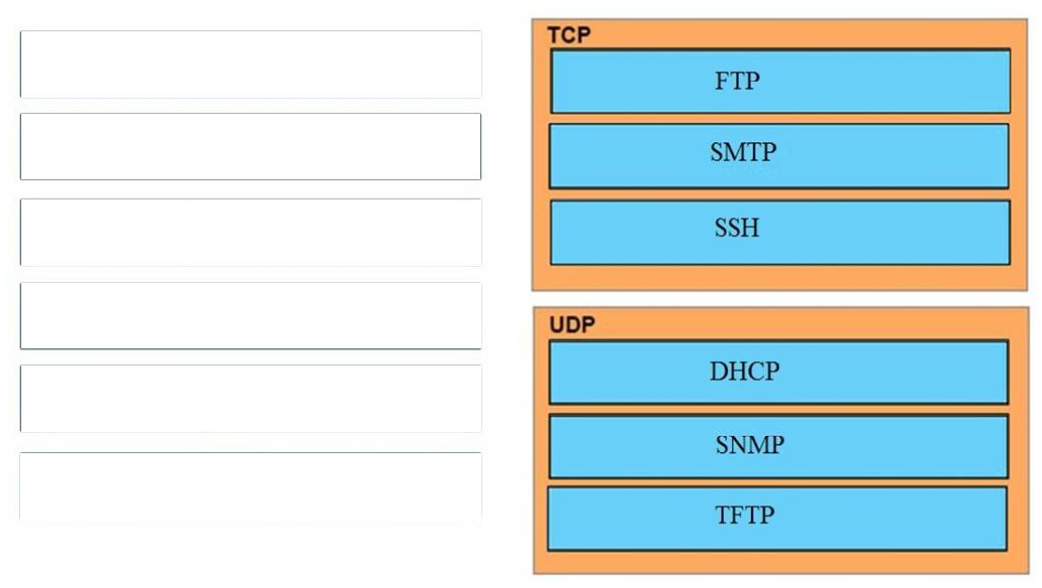
I.67. DRAG DROP. Drag and drop the application protocols from the left onto the transport protocols that is uses on the right.
Select and Place:
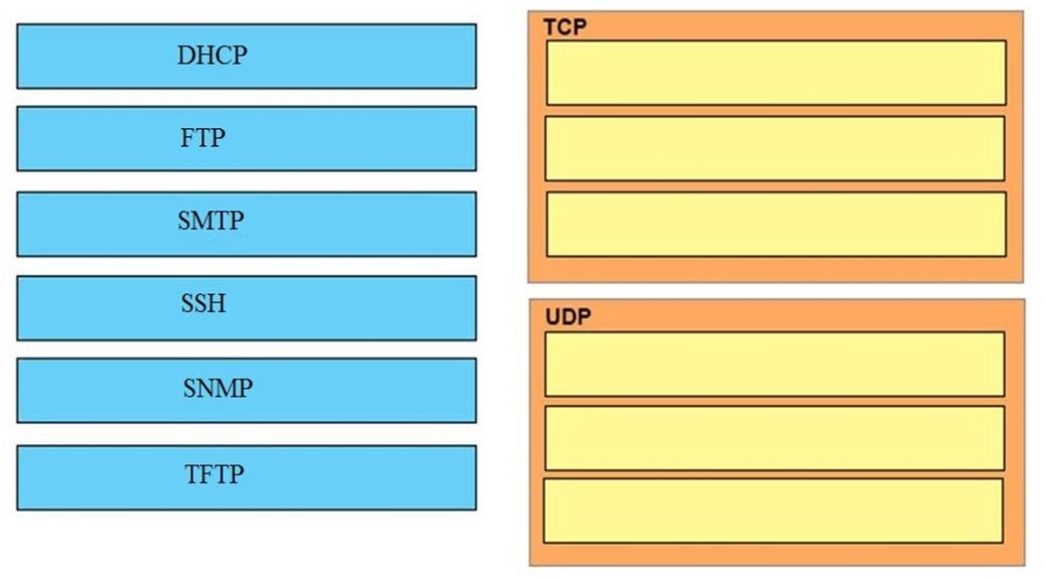
Correct Answer:
I.68. Which three encapsulation layers in the OSI model are combined into the TCP/IP application layer? (Choose three)
- Session
- transport
- presentation
- application
- data-link
- network
Show (Hide) Explanation/Reference
I.69. When is the most appropriate time to escalate an issue that you troubleshooting?
- When you lack the proper to resolve the issue
- When a more urgent issue that requires your intervention is detected
- When you have gathered all information about an issue
- When you have been unable to resolve the issue after 30 min
Show (Hide) Explanation/Reference
From this paragraph:
Step 2.Resolve orescalate: Problem isolation should eventually uncover the root cause of the problem – that is, the cause which, if fixed, will resolve the problem. In short, resolving the problem means finding the root cause of the problem and fixing that problem. Of course,what do you do if you cannot find the root cause, or fix (resolve) that root cause once found? Escalate the problem. Most companies have a defined escalation process, with different levels of technical support and management support depending on whether the next step requires more technical expertise or management decision making.
Reference: ICND1 100-105 Official Cert Guide
Also from this link: http://www.ciscopress.com/articles/article.asp?p=1578504&seqNum=2
"After you have clearly defined the problem, you have one more step to take before starting the actual troubleshooting process.You must determine whether this problem is your responsibility or if it needs to be escalated to another department or person. For example, assume the reported problem is this: "When user Y tries to access the corporate directory on the company intranet, she gets a message that says permission is denied. She can access all other intranet pages." You are a network engineer, and you do not have access to the servers. A separate department in your company manages the intranet servers. Therefore, you must know what to do when this type of problem is reported to you as a network problem. You must know whether to start troubleshooting or to escalate it to the server department. It is important that you know which type of problems is your responsibility to act on, what minimal actions you need to take before you escalate a problem, and how you escalate a problem."
So we can say answer A is the most suitable choice.
I.70. Which address class includes network 191.168.0.1/27?
- Class C
- Class B
- Class D
- Class A
Show (Hide) Explanation/Reference
This is a tricky question if you don't have a close look on the network. The first octet is 191, not 192 so it belongs to class B, not class C.
I.71. Which RFC was created to alleviate the depletion of IPv4 public addresses?
- RFC 4193
- RFC 1519
- RFC 1518
- RFC 1918
Show (Hide) Explanation/Reference
The RFC 1518 is Classless Interdomain Routing (CIDR), which is created to save the IPv4 addresses because we can now assign IP addresses classless. Therefore, instead of assigning the whole block of a class B or C address, now smaller blocks of a class can be assigned. For example, instead of assigning a whole block of 200.1.45.0/24, a smaller block, like 200.1.45.0/27 or 200.1.45.32/27, can be assigned.
The RFC 1918 is Address Allocation for Private Internets, which reserves IP addresses for private and internal use. These addresses can be used for networks that do not need to connect to the Internet.
Therefore the RFC 1918 is the best choice to "alleviate the depletion of IPv4 public addresses".
I.72. Which network topology allows all traffic to flow through a central hub?
- bus
- star
- mesh
- ring
Show (Hide) Explanation/Reference
Star topology is the most popular topology for the network which allows all traffic to flow through a central device.
I.73. Which statement about a router on a stick is true?
- Its date plane router traffic for a single VI AN over two or more switches.
- It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs on the same subnet
- It requires the native VLAN to be disabled.
- It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs.
Show (Hide) Explanation/Reference
https://www.freeccnaworkbook.com/workbooks/ccna/configuring-inter-vlan-routing-router-on-a-stick
I.74. Which component of the routing table ranks routing protocols according to their preferences?
- administrative distance
- next hop
- metric
- routing protocol code
Show (Hide) Explanation/Reference
Administrative distance – This is the measure of trustworthiness of the source of the route. If a router learns about a destination from more than one routing protocol, administrative distance is compared and the preference is given to the routes with lower administrative distance. In other words, it is the believability of the source of the route
I.75. Which two options are the best reasons to use an IPV4 private IP space?(choose two)
- to enable intra-enterprise communication
- to implement NAT
- to connect applications
- to conserve global address space
- to manage routing overhead
I.76. Assuming a subnet mask of 255.255.248.0, three of the following addresses are valid host addresses. Which are these addresses? (Choose three.)
- 172.16.9.0
- 172.16.8.0
- 172.16.31.0
- 172.16.20.0
Show (Hide) Explanation/Reference
From the subnet mask of 255.255.248.0 we learn that the increment is 8 therefore 172.16.8.0 is a network address which cannot be assigned to a host. Other network addresses are 172.16.16.0, 172.16.24.0, 172.16.32.0… Notice that 172.16.31.0 is a valid host address (which belongs to 172.16.24.0 to 172.16.31.255 subnet).
I.77. Which entity assigns IPv6 addresses to end users?
- ICANN
- APNIC
- RIR
- ISPs
Show (Hide) Explanation/Reference
According to the official IANA website "Users are assigned IP addresses by Internet service providers (ISPs). ISPs obtain allocations of IP addresses from a local Internet registry (LIR) or National Internet Registry (NIR), or from their appropriate Regional Internet Registry (RIR): https://www.iana.org/numbers
I.78. Which networking Technology is currently recognized as the standard for computer networking?
- System network architecture
- Transmission control protocol/Internet protocol
- Open system Interconnect
- Open network architecture
I.79. Which two tasks does the Dynamic Host Configuration Protocol perform? (Choose two.)
- Set the IP gateway to be used by the network.
- Perform host discovery used DHCPDISCOVER message.
- Configure IP address parameters from DHCP server to a host.
- Provide an easy management of layer 3 devices.
- Monitor IP performance using the DHCP server.
- Assign and renew IP address from the default pool.
Show (Hide) Explanation/Reference
Explanation:
The Dynamic Host Configuration Protocol (DHCP) is a network protocol used to configure devices that are connected to a network (known as hosts) so they can communicate on that network using the Internet Protocol (IP). It involves clients and a server operating in a client-server model. DHCP servers assigns IP addresses from a pool of addresses and also assigns other parameters such as DNS and default gateways to hosts.
I.80. Which statement about IPv6 link-local addresses is true ?
- They must be configured on all IPv6 interface
- They must be globally unique
- They must be manually configured
- They are advertised globally on the network
Show (Hide) Explanation/Reference
Link-local addresses refer only to a particular physical link and are used for addressing on a single link for purposes such as automatic address configuration and neighbor discovery protocol. Link-local addresses can be used to reach the neighboring nodes attached to the same link. The nodes do not need a globally unique address to communicate. Routers will not forward datagram using link-local addresses.All IPv6 enabled interfaces have a link-local unicast address.
A link-local address is an IPv6 unicast address that can be automatically configured on any interface using the link-local prefixFE80::/10 (1111 1110 10) and the interface identifier in the modified EUI-64 format. Link-local addresses are not necessarily bound to the MAC address (configured in a EUI-64 format). Link-local addresses can also be manually configured in the FE80::/10 format using the "ipv6 address link-local" command.
Reference: http://www.cisco.com/c/en/us/support/docs/ip/ip-version-6-ipv6/113328-ipv6-lla.html
In summary, if you do not configure a link-local on an IPv6 enabled interface, it will automatically use the FE80::/10 and the interface identifier in the modified EUI-64 format to form a link-local address.
I.81. Which header field is new on IPv6?
- Version
- Hop Limit
- Flow Label
- Traffic Class
Show (Hide) Explanation/Reference
Only three connection types are commonly known and used in Internet Protocol version four (IPv4) networks: unicast, multicast and broadcast. A fourth connection type, Anycast, was unknown until IPv6 made it a standard connection type. Anycast is not standardized in IPv4 but can be emulated. IPv4 Anycast addressing is a good solution to provide localization for services and servers in order to obtain robustness, redundancy and resiliency.
The basic idea of Anycast is very simple: multiple servers, which share the same IP address, host the same service. The routing infrastructure sends IP packets to the nearest server (according to the metric of the routing protocol used). The major benefits of employing Anycast in IPv4 are improved latency times, server load balancing, and improved security.
Reference: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.116.6367&rep=rep1&type=pdf
I.82. Which two statements about access points are true? (Choose Two)
- They can provide access within enterprises and to the public.
- in Most cases, they are physically connected to other network devices to provide network connectivity
- They can protect a network from internal and external threats.
- Most access points provide Wi-Fi and Bluetooth connectivity.
- They must be hardwired to a modem.
I.83. Which two statements describe characteristics of IPv6 unicast addressing? (Choose two.)
- Global addresses start with 2000::/3.
- Link-local addresses start with FE00:/12.
- Link-local addresses start with FF00::/10.
- There is only one loopback address and it is ::1.
- If a global address is assigned to an interface, then that is the only allowable address for the interface.
Show (Hide) Explanation/Reference
Below is the list of common kinds of IPv6 addresses:
| Loopback address | ::1 |
| Link-local address | FE80::/10 |
| Site-local address | FEC0::/10 |
| Global address | 2000::/3 |
| Multicast address | FF00::/8 |
From the above table, we learn that A and D are correct while B and C are incorrect. Notice that the IPv6 unicast loopback address is equivalent to the IPv4 loopback address, 127.0.0.1. The IPv6 loopback address is 0:0:0:0:0:0:0:1, or ::1.
E is not correct because of anycast addresses which are indistinguishable from normal unicast addresses. You can think of anycast addresses like this: "send it to nearest one which have this address". An anycast address can be assigned to many interfaces and the first interface receives the packet destined for this anycast address will proceed the packet. A benefit of anycast addressing is the capability to share load to multiple hosts. An example of this benefit is if you are a Television provider with multiple servers and you want your users to use the nearest server to them then you can use anycast addressing for your servers. When the user initiates a connection to the anycast address, the packet will be routed to the nearest server (the user does not have to specify which server they want to use).
I.84. Which three statements about IPv6 address fd14:920b:f83d:4079::/64 are true? (Choose three)
- The subnet ID is 14920bf83d
- The subnet ID is 4079
- The global ID is 14920bf83d
- The address is a link-local address
- The global ID is 4079
- The address is a unique local address
Show (Hide) Explanation/Reference
Let's see an example of IPv6 prefix: 2001:0A3C:5437:ABCD::/64:

In this example, the RIR has been assigned a 12-bit prefix. The ISP has been assigned a 32-bit prefix and the site is assigned a 48-bit site ID. The next 16-bit is the subnet field and it can allow 216, or 65536 subnets. This number is redundant for largest corporations on the world!
The 64-bit left (which is not shown the above example) is the Interface ID or host part and it is much more bigger: 64 bits or 264 hosts per subnet!
Therefore in this question 4079 is the subnet ID. The FD14 prefix belongs to FC00::/7 which is an IPv6 Unique Local Address (The address block fc00::/7 is divided into two /8 groups which are FC00::/8 & FD00::/8)
I.85. Which tunneling mechanism embeds an IPv4 address within an IPv6 address?
- Teredo
- 6to4
- 4to6
- GRE
- ISATAP
I.86. Which of the following statements describe the network shown in the graphic? (Choose two.)
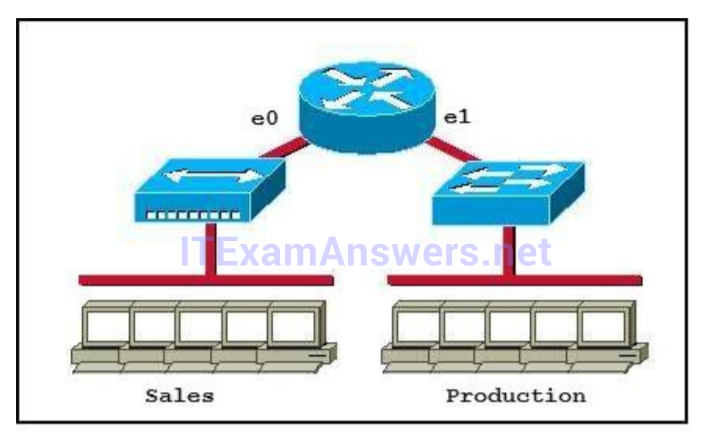
- There are two broadcast domains in the network.
- There are four broadcast domains in the network.
- There are six broadcast domains in the network.
- There are four collision domains in the network.
- There are five collision domains in the network.
- There are seven collision domains in the network.
Show (Hide) Explanation/Reference
Only router can break up broadcast domains so in the exhibit there are 2 broadcast domains: from e0 interface to the left is a broadcast domain and from e1 interface to the right is another broadcast domain -> A is correct.
Both router and switch can break up collision domains so there is only 1 collision domain on the left of the router (because hub doesn't break up collision domain) and there are 6 collision domains on the right of the router (1 collision domain from e1 interface to the switch + 5 collision domains for 5 PCs in Production) -> F is correct.
I.87. Which protocol does ipv6 use to discover other ipv6 nodes on the same segment?
- CLNS
- TCPv6
- NHRP
- NDP
- ARP
Show (Hide) Explanation/Reference
I.88. What is the most efficient subnet mask for a point to point ipv6 connection?
- /127
- /128
- /64
- /48
- /32
Show (Hide) Explanation/Reference
On inter-router point-to-point links, it is useful, for security and other reasons, to use 127-bit IPv6 prefixes. Such a practice parallels the use of 31-bit prefixes in IPv4.
Reference: https://tools.ietf.org/html/rfc6164
I.89. What are three features of the IPV6 protocol?(choose three)
- complicated header
- plug-and-play
- no broadcasts
- checksums
- optional IPsec
- autoconfiguration
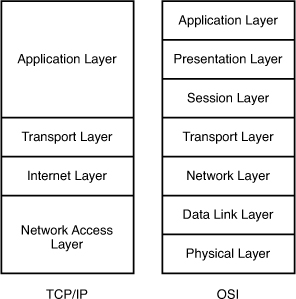
I.90. Where does routing occur within the DoD TCP/IP reference model?
- application
- internet
- network
- transport
Show (Hide) Explanation/Reference
The picture below shows the comparison between TCP/IP model & OSI model. Notice that the Internet Layer of TCP/IP is equivalent to the Network Layer which is responsible for routing decision.
I.91. Which address block identifies all link-local addresses?
- FC00::/7
- FC00::/8
- FE80::/10
- FF00::/8
Show (Hide) Explanation/Reference
Link-local addresses only used for communications within the local subnetwork (automatic address configuration, neighbor discovery, router discovery, and by many routing protocols). It is only valid on the current subnet. It is usually created dynamically using a link-local prefix of FE80::/10 and a 64-bit interface identifier (based on 48-bit MAC address).
I.92. For which two reasons was RFC 1918 address space define (Choose two)
- to preserve public IPv4 address space
- to reduce the occurrence of overlapping IP addresses
- to preserve public IPv6 address space
- reduce the size of ISP routing tables
- to support the NAT protocol
Show (Hide) Explanation/Reference
The RFC 1518 is Classless Interdomain Routing (CIDR). CIDR is a mechanism developed to help alleviate the problem of exhaustion of IP addresses and growth of routing tables.
The problems were:
+ With the classful routing system, individual networks were either limited to 254 hosts (/24) or 65,534 hosts (/16). For many network enterprises, 254 hosts were not enough and 65,534 were too large to be used efficiently.
+ Routing information overload. The size and rate of growth of the routing tables in Internet routers is beyond the ability of current software (and people) to effectively manage.
+ Eventual exhaustion of IP network numbers.
To solve these problem, CIDR was selected as the solution in 1992.
In contrast to classful routing, which categorizes addresses into one of three blocks, CIDR allows for blocks of IP addresses to be allocated to Internet service providers. The blocks are then split up and assigned to the provider's customers.
According to the CIDR standard, the first part of an IP address is a prefix, which identifies the network. The prefix is followed by the host identifier so that information packets can be sent to particular computers within the network. A CIDR address includes the standard 32-bit IP address and also the network prefix. For example, a CIDR address of 200.1.45.2/26, the "/26" indicates the first 26 bits are used to identify the unique network, leaving the remaining bits to identify the specific hosts.
Therefore, instead of assigning the whole block of a class B or C address, now smaller blocks of a class can be assigned. For example, instead of assigning a whole block of 200.1.45.0/24, a smaller block, like 200.1.45.0/27 or 200.1.45.32/27, can be assigned.
I.93. In which two circumstances are private IPv4 addresses appropriate? (Choose two)
- on internal hosts that stream data solely to external resources
- on hosts that communicates only with other internal hosts
- on the public-facing interface of a firewall
- on hosts that require minimal access to external resources
- to allow hosts inside an enterprise to communicate in both directions with hosts outside the enterprise
I.94. DRAG DROP. Drag and drop the IEEE standard cable names from the left onto the correct cable types on the right.
Select and Place:
Correct Answer:

I.95. Which major IPv6 address type is supported in IPv4 but rarely used?
- Broadcast
- Anycast
- Unicast
- Multicast
I.96. Refer to the exhibit, you determine that Computer A cannot ping Computer. Which reason for the problem is most likely true?
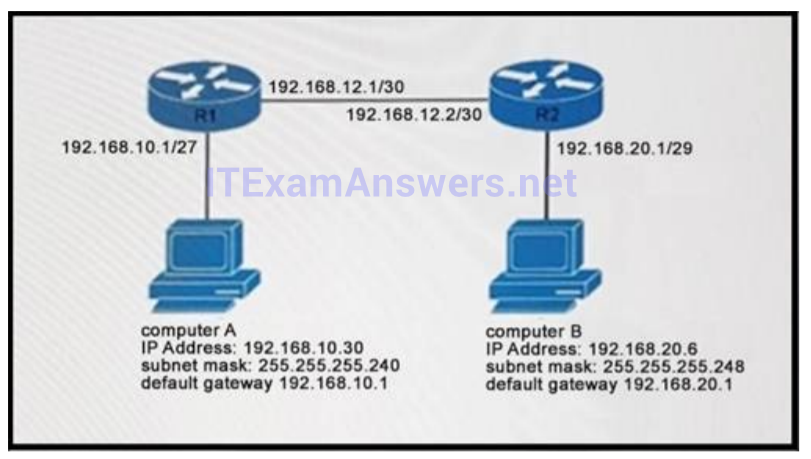
- The Subnet mask for Computer A is incorrect.
- The default gateway address for Computer A is incorrect.
- The subnet mask for computer B is incorrect.
- The default gateway address for computer B is incorrect.
Show (Hide) Explanation/Reference
255.255.255.224 = /27
I.97. Which option is a valid IPv6 address?
- 2001:0000:130F::099a::12a
- 2002:7654:A1AD:61:81AF:CCC1
- FEC0:2927:1860:W067::2A4
- 2004:1:25A4:886F::1
I.98. Refer to the exhibit. A new subnet with 60 hosts has been added to the network. Which subnet address should this network use to provide enough usable addresses while wasting the fewest addresses?
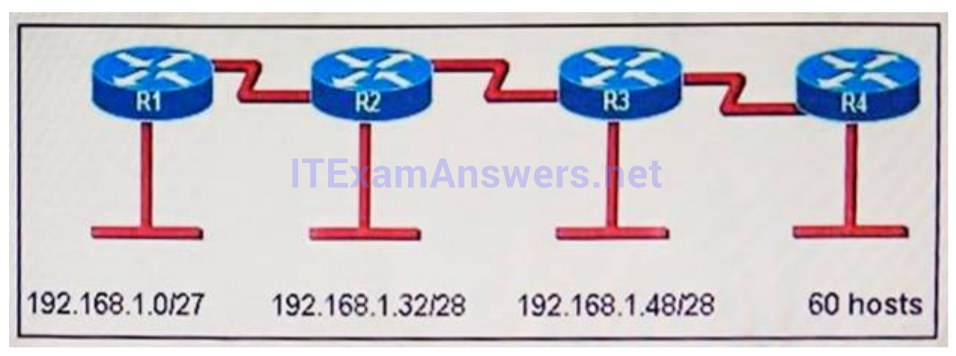
- 192.168.1.56/27
- 192.168.1.64/26
- 192.168.1.64/27
- 192.168.1.56/26
I.99. DRAG DROP. A user is unable to connect to the Internet. Based on the layered approach to troubleshooting and beginning with the lowest layer, drag each procedure on the left to its proper category on the right.
Select and Place:
Correct Answer:
I.100. Refer to the exhibit. Which subnet mask will place all hosts on Network B in the same subnet with the least amount of wasted addresses?
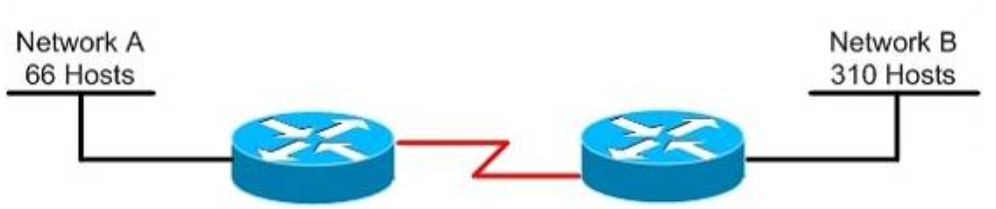
- 255.255.255.0
- 255.255.254.0
- 255.255.252.0
- 255.255.248.0
Show (Hide) Explanation/Reference
310 hosts < 512 = 29 -> We need a subnet mask of 9 bits 0 -> 1111 1111.1111 1111.1111 1110.0000 0000 -> 255.255.254.0
I.101. Which two are features of IPv6?(choose two)
- multicast
- broadcast
- allcast
- podcast
- anycast
Show (Hide) Explanation/Reference
IPv6 addresses are classified by the primary addressing and routing methodologies common in networkinG.
unicast addressing, anycast addressing, and multicast addressing.
I.102. Given an IP address 172.16.28.252 with a subnet mask of 255.255.240.0, what is the correct network address?
- 172.16.16.0
- 172.16.0.0
- 172.16.24.0
- 172.16.28.0
Show (Hide) Explanation/Reference
For this example, the network range is 172.16.16.1 – 172.16.31.254, the network address is 172.16.16.0 and
the broadcast IP address is 172.16.31.255.
I.103. Which IPv6 address is the equivalent of the IPv4 interface loopback address 127.0.0.1?
- ::1
- ::
- 2000::/3
- 0::/10
Show (Hide) Explanation/Reference
In IPv6 the loopback address is written as,
This is a 128bit number, with the first 127 bits being '0' and the 128th bit being '1'. It's just a single address, so
could also be written as ::1/128.
I.104. You are working in a data center environment and are assigned the address range 10.188.31.0/23. You are asked to develop an IP addressing plan to allow the maximum number of subnets with as many as 30 hosts each. Which IP address range meets these requirements?
- 10.188.31.0/26
- 10.188.31.0/25
- 10.188.31.0/25
- 10.188.31.0/27
- 10.188.31.0/29
Show (Hide) Explanation/Reference
Each subnet has 30 hosts < 32 = 25 so we need a subnet mask which has at least 5 bit 0s -> /27. Also the
question requires the maximum number of subnets (which minimum the number of hosts- per-subnet) so /27
is the best choice -> .
I.105. A network administrator is verifying the configuration of a newly installed host by establishing an FTP connection to a remote server. What is the highest layer of the protocol stack that the network administrator is using for this operation?
- application
- presentation
- session
- transport
- internet
- data link
Show (Hide) Explanation/Reference
FTP belongs to Application layer and it is also the highest layer of the OSI model.
I.106. A receiving host computes the checksum on a frame and determines that the frame is damaged. The frame is then discarded. At which OSI layer did this happen?
- session
- transport
- network
- data link
- physical
Show (Hide) Explanation/Reference
The Data Link layer provides the physical transmission of the data and handles error notification, network topology, and flow control. The Data Link layer formats the message into pieces, each called a data frame, and adds a customized header containing the hardware destination and source address. Protocols Data Unit (PDU) on Datalink layer is called frame. According to this question the frame is damaged and discarded which will happen at the Data Link layer.
I.107. Which two statements correctly describe steps in the OSI data encapsulation process? (Choose two.)
- The transport layer divides a data stream into segments and may add reliability and flow control information.
- The data link layer adds physical source and destination addresses and an FCS to the segment.
- Packets are created when the network layer encapsulates a frame with source and destination host addresses and protocol-related control information.
- Packets are created when the network layer adds Layer 3 addresses and control information to a segment.
- The presentation layer translates bits into voltages for transmission across the physical link.
Show (Hide) Explanation/Reference
The Application Layer (Layer 7) refers to communications services to applications and is the interface between the network and the application. Examples include. Telnet, HTTP, FTP, Internet browsers, NFS, SMTP gateways, SNMP, X.400 mail, and FTAM. The Presentation Layer (Layer 6) defining data formats, such as ASCII text, EBCDIC text, binary, BCD, and JPEG. Encryption also is defined as a presentation layer service. Examples include. JPEG, ASCII, EBCDIC, TIFF, GIF, PICT, encryption, MPEG, and MIDI. The Session Layer (Layer 5) defines how to start, control, and end communication sessions.
This includes the control and management of multiple bidirectional messages so that the application can be notified if only some of a series of messages are completed. This allows the presentation layer to have a seamless view of an incoming stream of data. The presentation layer can be presented with data if all flows occur in some cases. Examples include. RPC, SQL, NFS, NetBios names, AppleTalk ASP, and DECnet SCP The Transport Layer (Layer 4) defines several functions, including the choice of protocols. The most important Layer 4 functions are error recovery and flow control. The transport layer may provide for retransmission, i.e., error recovery, and may use flow control to prevent unnecessary congestion by attempting to send data at a rate that the network can accommodate, or it might not, depending on the choice of protocols. Multiplexing of incoming data for different flows to applications on the same host is also performed. Reordering of the incoming data stream when packets arrive out of order is included. Examples include. TCP, UDP, and SPX.
The Network Layer (Layer 3) defines end-to-end delivery of packets and defines logical addressing to accomplish this. It also defines how routing works and how routes are learned; and how to fragment a packet into smaller packets to accommodate media with smaller maximum transmission unit sizes. Examples include. IP, IPX, AppleTalk DDP, and ICMP. Both IP and IPX define logical addressing, routing, the learning of routing information, and end-to-end delivery rules. The IP and IPX protocols most closely match the OSI network layer (Layer 3) and are called Layer 3 protocols because their functions most closely match OSI's Layer 3. The Data Link Layer (Layer 2) is concerned with getting data across one particular link or medium. The data link protocols define delivery across an individual link. These protocols are necessarily concerned with the type of media in use. Examples includE. IEEE 802.3/802.2, HDLC, Frame Relay, PPP, FDDI, ATM,and IEEE 802.5/802.2.
I.108. Refer to the graphic. Host A is communicating with the server. What will be the source MAC address of the frames received by Host A from the server?
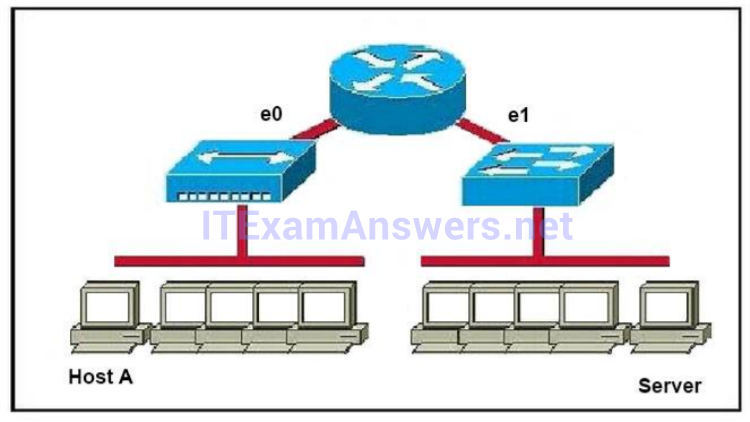
- the MAC address of router interface e0
- the MAC address of router interface e1
- the MAC address of the server network interface
- the MAC address of host A
Show (Hide) Explanation/Reference
Whereas switches can only examine and forward packets based on the contents of the MAC header, routers can look further into the packet to discover the network for which a packet is destined. Routers make forwarding decisions based on the packet's network-layer header (such as an IPX header or IP header). These network-layer headers contain source and destination network addresses. Local devices address packets to the router's MAC address in the MAC header. After receiving the packets, the router must perform the following steps:
1. Check the incoming packet for corruption, and remove the MAC header. The router checks the packet for MAC-layer errors. The router then strips off the MAC header and examines the network- layer header to determine what to do with the packet.
2. Examine the age of the packet. The router must ensure that the packet has not come too far to be forwarded. For example, IPX headers contain a hop count. By default, 15 hops is the maximum number of hops (or routers) that a packet can cross. If a packet has a hop count of 15, the router discards the packet. IP headers contain a Time to Live (TTL) value. Unlike the IPX hop count, which increments as the packet is forwarded through each router, the IP TTL value decrements as the IP packet is forwarded through each router. If an IP packet has a TTL value of 1, the router discards the packet. A router cannot decrement the TTL value to 1 and then forward the packet.
3. Determine the route to the destination. Routers maintain a routing table that lists available networks, thedirection to the desired network (the outgoing interface number), and the distance to those networks. After determining which direction to forward the packet, the router must build a new header. (If you want to read the IP routing tables on a Windows 95/98 workstation, type ROUTE PRINT in the DOS box.)
4. Build the new MAC header and forward the packet. Finally, the router builds a new MAC header for the packet. The MAC header includes the router's MAC address and the final destination's MAC address or the MAC address of the next router in the path.
I.109. Refer to exhibit: Which destination addresses will be used by Host A to send data to Host C? (Choose two.)
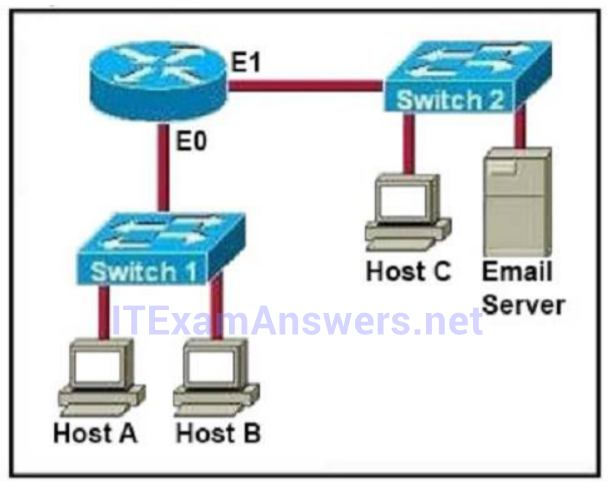
- the IP address of Switch 1
- the MAC address of Switch 1
- the IP address of Host C
- the MAC address of Host C
- the IP address of the router's E0 interface
- the MAC address of the router's E0 interface
Show (Hide) Explanation/Reference
While transferring data through many different networks, the source and destination IP addresses are not changed. Only the source and destination MAC addresses are changed. So in this case Host A will use the IP address of Host C and the MAC address of E0 interface to send data. When the router receives this data, it replaces the source MAC address with it own E1 interface's MAC address and replaces the destination MAC address with Host C's MAC address before sending to Host C.
I.110. At which layer of the OSI model is RSTP used to prevent loops?
- physical
- data link
- network
- transport
Show (Hide) Explanation/Reference
RSTP and STP operate on switches and are based on the exchange of Bridge Protocol Data Units (BPDUs) between switches. One of the most important fields in BPDUs is the Bridge Priority in which the MAC address is used to elect the Root Bridge -> RSTP operates at Layer 2 ?Data Link layer -> .
I.111. What does a Layer 2 switch use to decide where to forward a received frame?
- source MAC address
- source IP address
- source switch port
- destination IP address
- destination port address
- destination MAC address
Show (Hide) Explanation/Reference
When a frame is received, the switch looks at the destination hardware address and finds the interface if it is in its MAC address table. If the address is unknown, the frame is broadcast on all interfaces except the one it was received on.
I.112. Based on the network shown in the graphic. Which option contains both the potential networking problem and the protocol or setting that should be used to prevent the problem?
- routing loops, hold down timers
- switching loops, split horizon
- routing loops, split horizon
- switching loops, VTP
- routing loops, STP
- switching loops, STP
Show (Hide) Explanation/Reference
The Spanning-Tree Protocol (STP) prevents loops from being formed when switches or bridges are interconnected via multiple paths. Spanning-Tree Protocol implements the 802.1D IEEE algorithm by exchanging BPDU messages with other switches to detect loops, and then removes the loop by shutting down selected bridge interfaces. This algorithm guarantees that there is one and only one active path between two network devices.
I.113. Refer to the exhibit. The network administrator normally establishes a Telnet session with the switch from host A. However, host A is unavailable. The administrator's attempt to telnet to the switch from host fails, but pings to the other two hosts are successful. What is the issue?
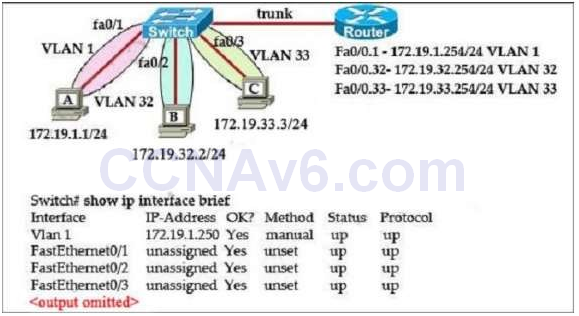
- The switch interfaces need the appropriate IP addresses assigned.
- Host and the switch need to be in the same subnet.
- The switch needs an appropriate default gateway assigned.
- The switch interface connected to the router is down.
- Host needs to be assigned an IP address in VLAN 1.
Show (Hide) Explanation/Reference
Host A (172.19.1.1) and the management IP address of the Switch (172.19.1.250) are in the same subnet so telnet from host A to the switch can be successful even if a default gateway is not set on host A.
But host B (172.19.32.2) and the management IP address of the Switch (172.19.1.250) are not in the same subnet. Therefore packets from host B must reach the router Fa0/0.32 interface before forwarding to the switch. But when the switch replies, it does not know how to send packets so an appropriate default gateway must be assigned on the switch (to Fa0/0.32 – 172.19.32.254).
Answer A is not correct because even when host B & the switch are in the same subnet, they cannot communicate because of different VLANs.
Answer C is not correct as host B can ping other two hosts.
Answer D is not correct because host B always belongs to VLAN 32 so assigning an IP address in VLAN 1 does not solve the problem.
I.114. What is the alternative notation for the IPv6 address B514:82C3:0000:0000:0029:EC7A:0000:EC72?
- B514 : 82C3 : 0029 : EC7A : EC72
- B514 : 82C3 :: 0029 : EC7A : EC72
- B514 : 82C3 : 0029 :: EC7A : 0000 : EC72
- B514 : 82C3 :: 0029 : EC7A : 0 : EC72
Show (Hide) Explanation/Reference
There are two ways that an IPv6 address can be additionally compressed: compressing leading zeros and substituting a group of consecutive zeros with a single double colon (::). Both of these can be used in any number of combinations to notate the same address. It is important to note that the double colon (::) can only be used once within a single IPv6 address notation. So, the extra 0's can only be compressed once.
I.115. Refer to the diagram. All hosts have connectivity with one another. Which statements describe the addressing scheme that is in use in the network? (Choose three.)
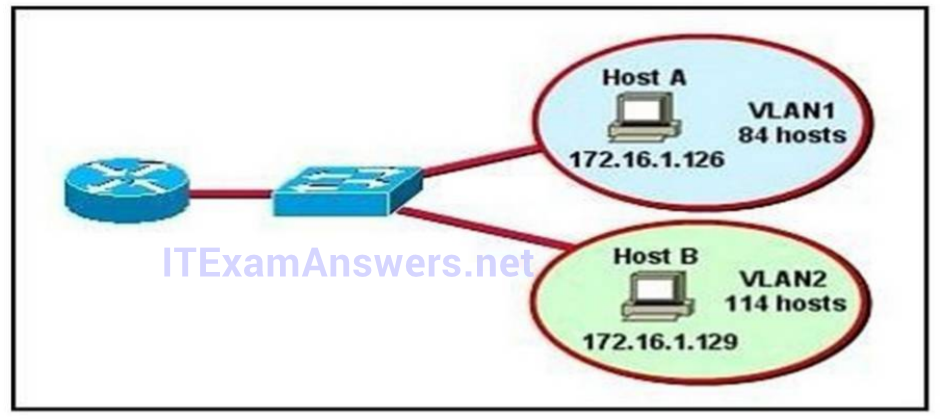
- The subnet mask in use is 255.255.255.192
- The subnet mask in use is 255.255.255.128
- The IP address 172.16.1.25 can be assigned to hosts in VLAN1
- The IP address 172.16.1.205 can be assigned to hosts in VLAN1
- The LAN interface of the router is configured with one IP address.
- The LAN interface of the router is configured with multiple IP addresses.
Show (Hide) Explanation/Reference
The subnet mask in use is 255.255.255.128: This is subnet mask will support up to 126 hosts, which is needed.
The IP address 172.16.1.25 can be assigned to hosts in VLAN1: The usable host range in this subnet is 172.16.1.1-172.16.1.126
The LAN interface of the router is configured with multiple IP addresses: The router will need 2 subinterfaces for the single physical interface, one with an IP address that belongs in each VLAN.
I.116. The network administrator has been asked to give reasons for moving from IPv4 to IPv6. What are two valid reasons for adopting IPv6 over IPv4? (Choose two.)
- no broadcast
- change of source address in the IPv6 header
- change of destination address in the IPv6 header
- Telnet access does not require a password
- autoconfiguration
- NAT
Show (Hide) Explanation/Reference
IPv6 does not use broadcasts, and autoconfiguration is a feature of IPV6 that allows for hosts to automatically obtain an IPv6 address.
I.117. An administrator must assign static IP addresses to the servers in a network. For network 192.168.20.24/29, the router is assigned the first usable host address while the sales server is given the last usable host address. Which of the following should be entered into the IP properties box for the sales server?
Correct Answer: C
Show (Hide) Explanation/Reference
For the 192.168.20.24/29 network, the usable hosts are 192.168.24.25 (router) ?192.168.24.30 (used for the sales server).
I.118. Which subnet mask would be appropriate for a network address range to be subnetted for up to eight LANs, with each LAN containing 5 to 26 hosts?
- 0.0.0.240
- 255.255.255.252
- 255.255.255.0
- 255.255.255.224
- 255.255.255.240
Show (Hide) Explanation/Reference
For a class C network, a mask of 255.255.255.224 will allow for up to 8 networks with 32 IP addresses each (30 usable).
I.119. How many bits are contained in each field of an IPv6 address?
- 24
- 4
- 8
- 16
Show (Hide) Explanation/Reference
An IPv6 address is represented as eight groups of four hexadecimal digits, each group representing 16 bits (two octets). The groups are separated by colons (:). An example of an IPv6 address is 2001:0db8:85a3:0000:0000:8a2e:0370:7334.
I.120. What are three approaches that are used when migrating from an IPv4 addressing scheme to an IPv6 scheme. (Choose three.)
- enable dual-stack routing
- configure IPv6 directly
- configure IPv4 tunnels between IPv6 islands
- use proxying and translation to translate IPv6 packets into IPv4 packets
- statically map IPv4 addresses to IPv6 addresses
- use DHCPv6 to map IPv4 addresses to IPv6 addresses
Show (Hide) Explanation/Reference
Several methods are used terms of migration including tunneling, translators, and dual stack. Tunnels are used to carry one protocol inside another, while translators simply translate IPv6 packets into IPv4 packets. Dual stack uses a combination of both native IPv4 and IPv6. With dual stack, devices are able to run IPv4 and IPv6 together and if IPv6 communication is possible that is the preferred protocol. Hosts can simultaneously reach IPv4 and IPv6 content.
I.121. Refer to the exhibit. In this VLSM addressing scheme, what summary address would be sent from router A?
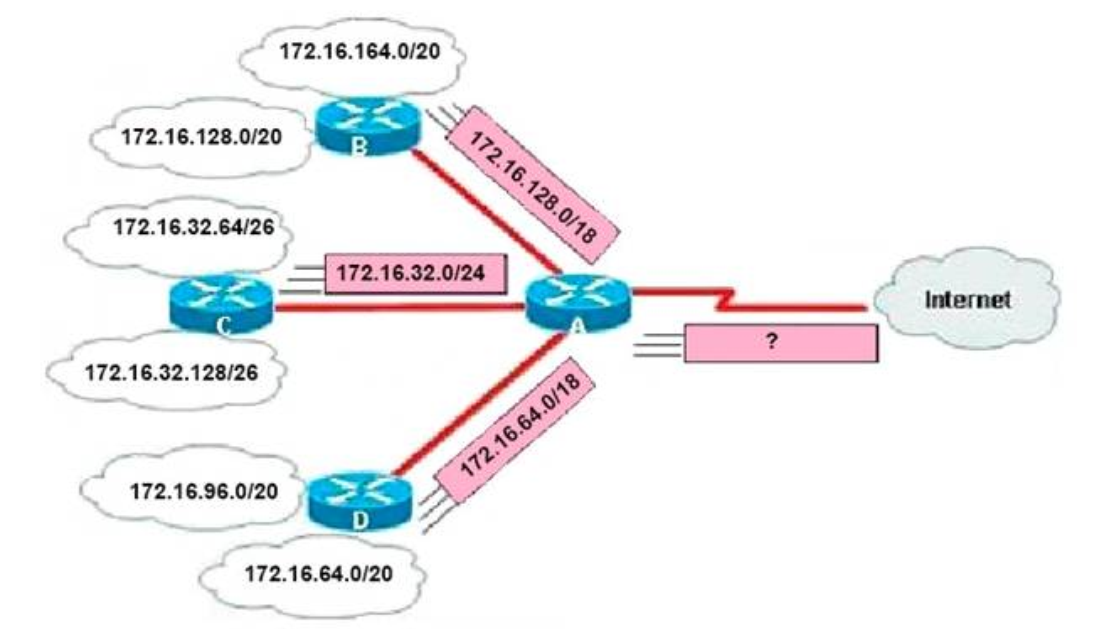
- 172.16.0.0 /16
- 172.16.0.0 /20
- 172.16.0.0 /24
- 172.32.0.0 /16
- 172.32.0.0 /17
- 172.64.0.0 /16
Show (Hide) Explanation/Reference
Router A receives 3 subnets: 172.16.64.0/18, 172.16.32.0/24 and 172.16.128.0/18. All these 3 subnets have the same form of 172.16.x.x so our summarized subnet must be also in that form -> Only A, B or. The smallest subnet mask of these 3 subnets is /18 so our summarized subnet must also have its subnet mask equal or smaller than /18. -> Only answer A has these 2 conditions ->
I.122. How is an EUI-64 format interface ID created from a 48-bit MAC address?
- by appending 0xFF to the MAC address
- by prefixing the MAC address with 0xFFEE
- by prefixing the MAC address with 0xFF and appending 0xFF to it
- by inserting 0xFFFE between the upper three bytes and the lower three bytes of the MAC address
- by prefixing the MAC address with 0xF and inserting 0xF after each of its first three bytes
Show (Hide) Explanation/Reference
The modified EUI-64 format interface identifier is derived from the 48-bit link-layer (MAC) address by inserting the hexadecimal number FFFE between the upper three bytes (OUI field) and the lower three bytes (serial number) of the link layer address.
I.123. Refer to the exhibit. What is the most efficient summarization that R1 can use to advertise its networks to R2?
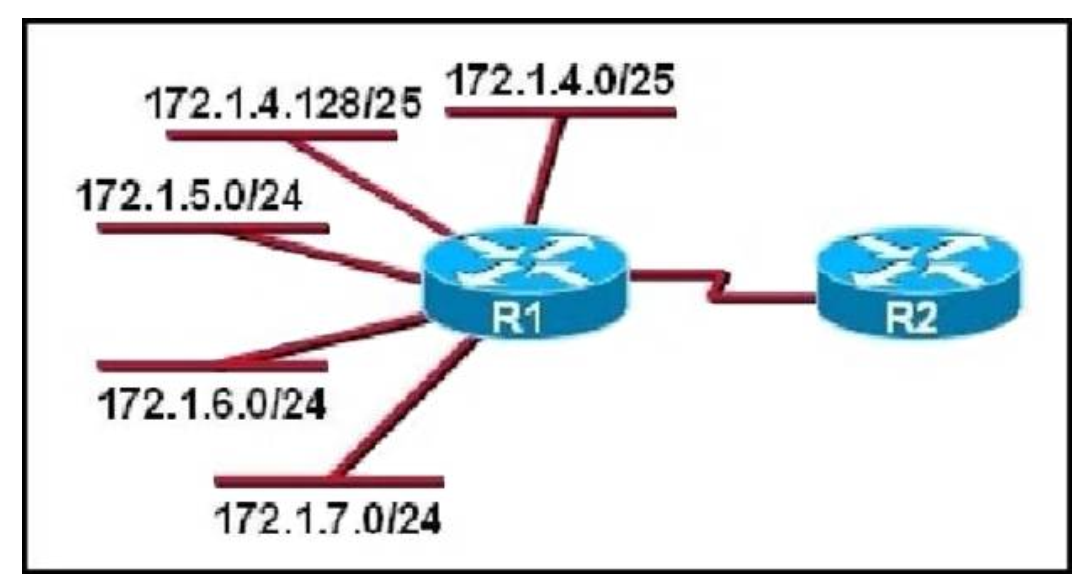
Show (Hide) Explanation/Reference
The 172.1.4.0/22 subnet encompasses all routes from the IP range 172.1.4.0 ?172.1.7.255.
I.124. Which three are characteristics of an IPv6 anycast address? (Choose three.)
- one-to-many communication model
- one-to-nearest communication model
- any-to-many communication model
- a unique IPv6 address for each device in the group
- the same address for multiple devices in the group
- delivery of packets to the group interface that is closest to the sending device
Show (Hide) Explanation/Reference
A new address type made specifically for IPv6 is called the Anycast Address. These IPv6 addresses are global addresses, these addresses can be assigned to more than one interface unlike an IPv6 unicast address. Anycast is designed to send a packet to the nearest interface that is a part of that anycast group. The sender creates a packet and forwards the packet to the anycast address as the destination address which goes to the nearest router. The nearest router or interface is found by using the metric of a routing protocol currently running on the network. However, in a LAN setting the nearest interface is found depending on the order the neighbors were learned. The anycast packet in a LAN setting forwards the packet to the neighbor it learned about first.
I.125. A national retail chain needs to design an IP addressing scheme to support a nationwide network. The company needs a minimum of 300 sub-networks and a maximum of 50 host addresses per subnet. Working with only one Class B address, which of the following subnet masks will support an appropriate addressing scheme? (Choose two.)
- 255.255.255.0
- 255.255.255.128
- 255.255.252.0
- 255.255.255.224
- 255.255.255.192
- 255.255.248.0
Show (Hide) Explanation/Reference
Subnetting is used to break the network into smaller more efficient subnets to prevent excessive rates of Ethernet packet collision in a large network. Such subnets can be arranged hierarchically, with the organization's network address space (see also Autonomous System) partitioned into a tree-like structure. Routers are used to manage traffic and constitute borders between subnets. A routing prefix is the sequence of leading bits of an IP address that precede the portion of the address used as host identifier. In IPv4 networks, the routing prefix is often expressed as a "subnet mask", which is a bit mask covering the number of bits used in the prefix. An IPv4 subnet mask is frequently expressed in quad-dotted decimal representation, e.g., 255.255.255.0 is the subnet mask for the 192.168.1.0 network with a 24-bit routing prefix (192.168.1.0/24).
I.126. Refer to the exhibit. A network administrator is adding two new hosts to Switch A . Which three values could be used for the configuration of these hosts? (Choose three.)
- host A IP address: 192.168.1.79
- host A IP address: 192.168.1.64
- host A default gateway: 192.168.1.78
- host B IP address: 192.168.1.128
- host B default gateway: 192.168.1.129
- host B IP address: 192.168.1.190
I.127. Which IPv6 address is the all-router multicast group?
- FF02::1
- FF02::2
- FF02::3
- FF02::4
Show (Hide) Explanation/Reference
Well-known IPv6 multicast addresses:
Address
Description
ff02::1
All nodes on the local network segment
ff02::2
All routers on the local network segment
I.128. Refer to the exhibit. Which address range efficiently summarizes the routing table of the addresses for router Main?
- 172.16.0.0./21
- 172.16.0.0./20
- 172.16.0.0./16
- 172.16.0.0/18
Show (Hide) Explanation/Reference
The 172.16.0.0./20 network is the best option as it includes all networks from 172.16.0.0 – 172.16.16.0 anddoes it more efficiently than the /16 and /18 subnets. The /21 subnet will not include all the other subnets in this one single summarized address.
I.129. Which IPv6 address is valid?
- 2001:0db8:0000:130F:0000:0000:08GC:140B
- 2001:0db8:0:130H::87C:140B
- 2031::130F::9C0:876A:130B
- 2031:0:130F::9C0:876A:130B
Show (Hide) Explanation/Reference
An IPv6 address is represented as eight groups of four hexadecimal digits, each group representing 16 bits (two octets). The groups are separated by colons (:). An example of an IPv6 address is 2001:0db8:85a3:0000:0000:8a2e:0370:7334. The leading 0's in a group can be collapsed using ::, but this can only be done once in an IP address.
I.130. Which command can you use to manually assign a static IPv6 address to a router interface?
- ipv6 autoconfig 2001:db8:2222:7272::72/64
- ipv6 address 2001:db8:2222:7272::72/64
- ipv6 address PREFIX_1 ::1/64
- ipv6 autoconfig
Show (Hide) Explanation/Reference
To assign an IPv6 address to an interface, use the "ipv6 address" command and specify the IP address you wish to use.
I.131. Which of these represents an IPv6 link-local address?
- FE80::380e:611a:e14f:3d69
- FE81::280f:512b:e14f:3d69
- FEFE:0345:5f1b::e14d:3d69
- FE08::280e:611:a:f14f:3d69
Show (Hide) Explanation/Reference
In the Internet Protocol Version 6 (IPv6), the address block fe80::/10 has been reserved for link- local unicast addressing. The actual link local addresses are assigned with the prefix fe80::/64. They may be assigned byautomatic (stateless) or stateful (e.g. manual) mechanisms.
I.132. Refer to the exhibit. What is the meaning of the output MTU 1500 bytes?
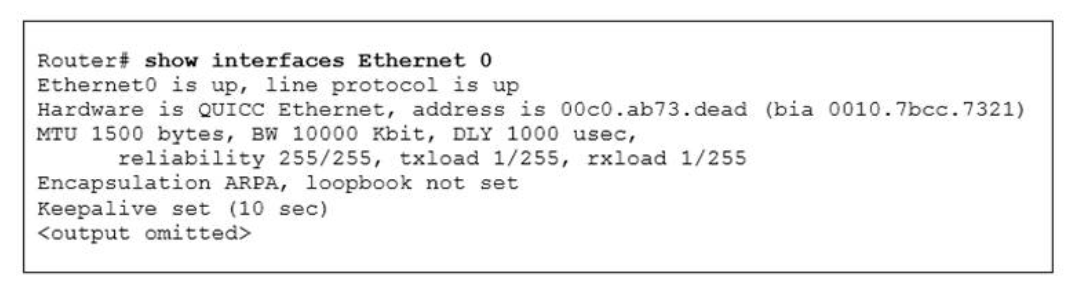
- The maximum number of bytes that can traverse this interface per second is 1500.
- The minimum segment size that can traverse this interface is 1500 bytes.
- The maximum segment size that can traverse this interface is 1500 bytes.
- The minimum packet size that can traverse this interface is 1500 bytes.
- The maximum packet size that can traverse this interface is 1500 bytes.
- The maximum frame size that can traverse this interface is 1500 bytes.
Show (Hide) Explanation/Reference
The Maximum Transmission Unit (MTU) defines the maximum Layer 3 packet (in bytes) that the layer can pass onwards.
I.133. On a corporate network, hosts on the same VLAN can communicate with each other, but they are unable to communicate with hosts on different VLANs. What is needed to allow communication between the VLANs?
- a router with subinterfaces configured on the physical interface that is connected to the switch
- a router with an IP address on the physical interface connected to the switch
- a switch with an access link that is configured between the switches
- a switch with a trunk link that is configured between the switches
Show (Hide) Explanation/Reference
Different VLANs can't communicate with each other, they can communicate with the help of Layer3 router. Hence, it is needed to connect a router to a switch, then make the sub-interface on the router to connect to the switch, establishing Trunking links to achieve communications of devices which belong to different VLANs.
When using VLANs in networks that have multiple interconnected switches, you need to use VLAN trunking between the switches. With VLAN trunking, the switches tag each frame sent between switches so that the receiving switch knows to what VLAN the frame belongs. End user devices connect to switch ports that provide simple connectivity to a single VLAN each.
The attached devices are unaware of any VLAN structure. By default, only hosts that are members of the same VLAN can communicate. To change this and allow interVLAN communication, you need a router or a layer 3 switch. Here is the example of configuring the router for inter-vlan communication RouterA(config)#int f0/0.1 RouterA(config-subif)#encapsulation ? dot1Q IEEE 802.1Q Virtual LAN RouterA(config-subif)#encapsulation dot1Q or isl VLAN ID RouterA(config-subif)# ip address x.x.x.x y.y.y.y
I.134. Refer to the exhibit. Users on the 172.17.22.0 network cannot reach the server located on the 172.31.5.0 network. The network administrator connected to router Coffee via the console port, issued the show ip route command, and was able to ping the server. Based on the output of the show ip route command and the topology shown in the graphic, what is the cause of the failure?
- The network has not fully converged.
- IP routing is not enabled.
- A static route is configured incorrectly.
- The FastEthernet interface on Coffee is disabled.
- The neighbor relationship table is not correctly updated.
- The routing table on Coffee has not updated.
Show (Hide) Explanation/Reference
The default route or the static route was configured with incorrect next-hop ip address 172.19.22.2 The correct ip address will be 172.18.22.2 to reach server located on 172.31.5.0 network. Ip route 0.0.0.0 0.0.0.0 172.18.22.2
I.135. Host 1 is trying to communicate with Host 2. The e0 interface on Router C is down. Which of the following are true? (Choose two.)
- Router C will use ICMP to inform Host 1 that Host 2 cannot be reached.
- Router C will use ICMP to inform Router B that Host 2 cannot be reached.
- Router C will use ICMP to inform Host 1, Router A, and Router B that Host 2 cannot be reached.
- Router C will send a Destination Unreachable message type.
- Router C will send a Router Selection message type.
- Router C will send a Source Quench message type.
Show (Hide) Explanation/Reference
Host 1 is trying to communicate with Host 2. The e0 interface on Router C is down. Router C will send ICMP packets to inform Host 1 that Host 2 cannot be reached.
I.136. Refer to the exhibit. A network technician is asked to design a small network with redundancy. The exhibit represents this design, with all hosts configured in the same VLAN. What conclusions can be made about this design?
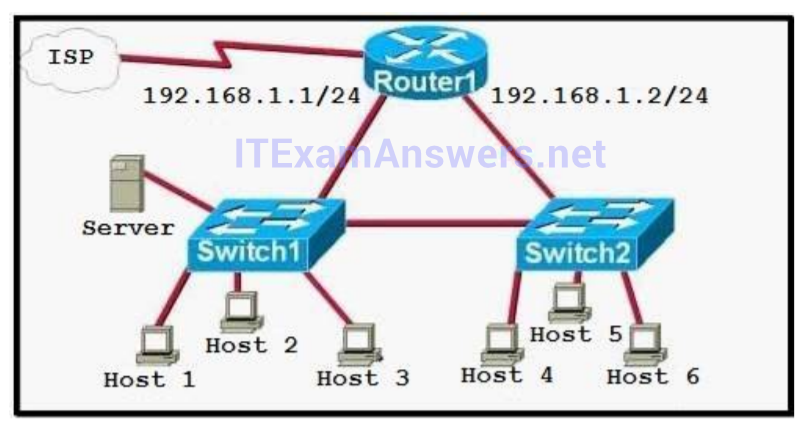
- The design will function as intended
- Spanning-tree will need to be used
- The router will not accept the addressing scheme
- The connection between switches should be a trunk.
- The router interfaces must be encapsulated with the 802.1Q protocol.
Show (Hide) Explanation/Reference
Each interface on a router must be in a different network. If two interfaces are in the same network, the router will not accept it and show error when the administrator assigns it.
I.137. In which circumstance are multiple copies of the same unicast frame likely to be transmitted in a switched LAN?
- during high traffic periods
- after broken links are re-established
- when upper-layer protocols require high reliability
- in an improperly implemented redundant topology
- when a dual ring topology is in use
Show (Hide) Explanation/Reference
If we connect two switches via 2 or more links and do not enable STP on these switches then a loop (which creates multiple copies of the same unicast frame) will occur. It is an example of an improperly implemented redundant topology.
I.138. The network shown in the diagram is experiencing connectivity problems. Which of the following will correct the problems? (Choose two.)
- Configure the gateway on Host A as 10.1.1.1
- Configure the gateway on Host B as 10.1.2.254
- Configure the IP address of Host A as 10.1.2.2
- Configure the IP address of Host B as 10.1.2.2
- Configure the masks on both hosts to be 255.255.255.224
- Configure the masks on both hosts to be 255.255.255.240
Show (Hide) Explanation/Reference
The switch 1 is configured with two VLANs: VLAN1 and VLAN2. The IP information of member Host A in VLAN1 is as follows:
Address : 10.1.1.126
Mask : 255.255.255.0
Gateway : 10.1.1.254
The IP information of member Host B in VLAN2 is as follows:
Address : 10.1.1.12
Mask : 255.255.255.0
Gateway : 10.1.1.254
The configuration of sub-interface on router 2 is as follows:
Fa0/0.1 — 10.1.1.254/24 VLAN1
Fa0/0.2 — 10.1.2.254/24 VLAN2
It is obvious that the configurations of the gateways of members in VLAN2 and the associated network segments are wrong. The layer3 addressing information of Host B should be modified as follows:
Address : 10.1.2.X
Mask : 255.255.255.0
I.139. Refer to the exhibit. A problem with network connectivity has been observed. It is suspected that the cable connected to switch port Fa0/9 on Switch1 is disconnected. What would be an effect of this cable being disconnected?
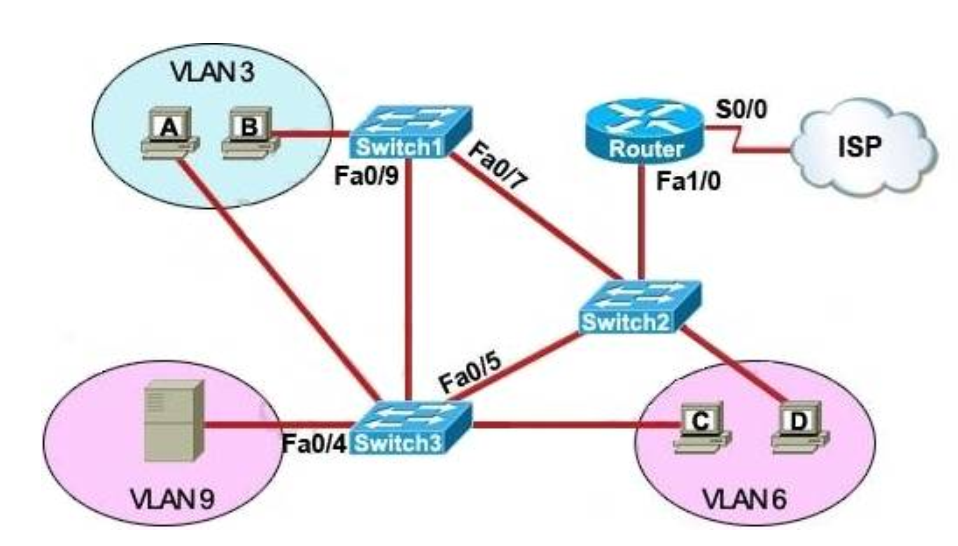
- Host B would not be able to access the server in VLAN9 until the cable is reconnected.
- Communication between VLAN3 and the other VLANs would be disabled.
- The transfer of files from Host B to the server in VLAN9 would be significantly slower.
- For less than a minute, Host B would not be able to access the server in VLAN9. Then normal network function would resume.
Show (Hide) Explanation/Reference
Spanning-Tree Protocol (STP) is a Layer 2 protocol that utilizes a special-purpose algorithm to discover physical loops in a network and effect a logical loop-free topology. STP creates a loop- free tree structure consisting of leaves and branches that span the entire Layer 2 network. The actual mechanics of how bridges communicate and how the STP algorithm works will be discussed at length in the following topics. Note that the terms bridge and switch are used interchangeably when discussing STP. In addition, unless otherwise indicated, connections between switches are assumed to be trunks
I.140. Refer to the exhibit. HostA cannot ping HostB. Assuming routing is properly configured, what is the cause of this problem?
- HostA is not on the same subnet as its default gateway.
- The address of SwitchA is a subnet address.
- The Fa0/0 interface on RouterA is on a subnet that can't be used.
- The serial interfaces of the routers are not on the same subnet.
- The Fa0/0 interface on RouterB is using a broadcast address.
Show (Hide) Explanation/Reference
Now let's find out the range of the networks on serial link:
For the network 192.168.1.62/27:
Increment: 32
Network address: 192.168.1.32
Broadcast address: 192.168.1.63
For the network 192.168.1.65/27:
Increment: 32
Network address: 192.168.1.64
Broadcast address: 192.168.1.95
-> These two IP addresses don't belong to the same network and they can't see each other
I.141. Refer to the exhibit. The two connected ports on the switch are not turning orange or green. What would be the most effective steps to troubleshoot this physical layer problem? (Choose three.)
- Ensure that the Ethernet encapsulations match on the interconnected router and switch ports.
- Ensure that cables A and B are straight-through cables.
- Ensure cable A is plugged into a trunk port.
- Ensure the switch has power.
- Reboot all of the devices.
- Reseat all cables.
Show (Hide) Explanation/Reference
The ports on the switch are not up indicating it is a layer 1 (physical) problem so we should check cable type, power and how they are plugged in.
I.142. Refer to the exhibit. A network administrator attempts to ping Host2 from Host1 and receives the results that are shown. What is the problem?
- The link between Host1 and Switch1 is down.
- TCP/IP is not functioning on Host1
- The link between Router1 and Router2 is down.
- The default gateway on Host1 is incorrect.
- Interface Fa0/0 on Router1 is shutdown.
- The link between Switch1 and Router1 is down.
Show (Hide) Explanation/Reference
Host1 tries to communicate with Host2. The message destination host unreachable from Router1 indicates that the problem occurs when the data is forwarded from Host1 to Host2. According to the topology, we can infer that The link between Router1 and Router2 is down.
I.143. Refer to the exhibit. Hosts in network 192.168.2.0 are unable to reach hosts in network 192.168.3.0. Based on the output from RouterA, what are two possible reasons for the failure? (Choose two.)
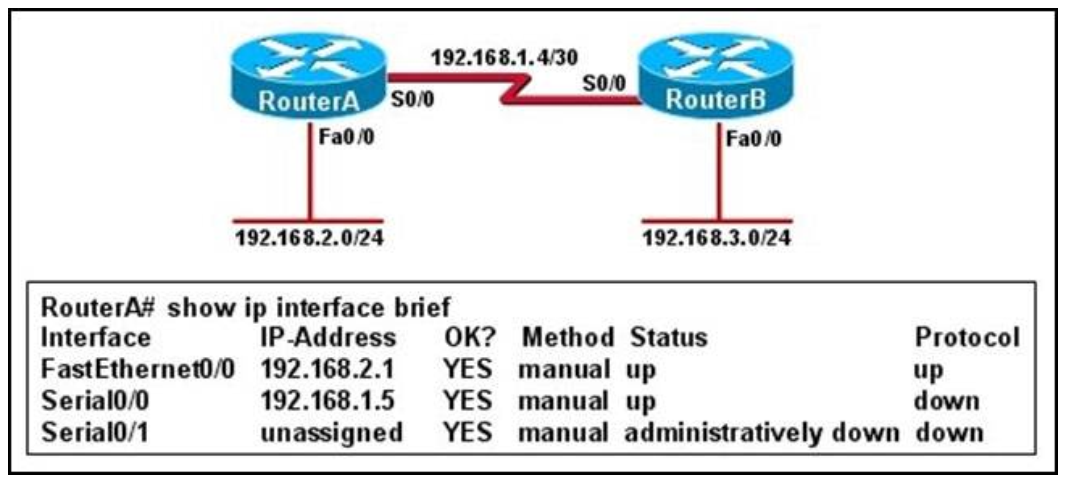
- The cable that is connected to S0/0 on RouterA is faulty.
- Interface S0/0 on RouterB is administratively down.
- Interface S0/0 on RouterA is configured with an incorrect subnet mask.
- The IP address that is configured on S0/0 of RouterB is not in the correct subnet.
- Interface S0/0 on RouterA is not receiving a clock signal from the CSU/DSU.
- The encapsulation that is configured on S0/0 of RouterB does not match the encapsulation that is configured on S0/0 of RouterA
Show (Hide) Explanation/Reference
From the output we can see that there is a problem with the Serial 0/0 interface. It is enabled, but the line protocol is down. The could be a result of mismatched encapsulation or the interface not receiving a clock signal from the CSU/ DSU.
I.144. Refer to the exhibit. An administrator pings the default gateway at 10.10.10.1 and sees the output as shown. At which OSI layer is the problem?
- data link layer
- application layer
- access layer
- session layer
- network layer
Show (Hide) Explanation/Reference
The command ping uses ICMP protocol, which is a network layer protocol used to propagate control message between host and router. The command ping is often used to verify the network connectivity, so it works at the network layer.
I.145. Refer to the exhibit. What will Router1 do when it receives the data frame shown? (Choose three.)
- Router1 will strip off the source MAC address and replace it with the MAC address 0000.0c36.6965.
- Router1 will strip off the source IP address and replace it with the IP address 192.168.40.1.
- Router1 will strip off the destination MAC address and replace it with the MAC address 0000.0c07.4320.
- Router1 will strip off the destination IP address and replace it with the IP address of 192.168.40.1.
- Router1 will forward the data packet out interface FastEthernet0/1.
- Router1 will forward the data packet out interface FastEthernet0/2.
Show (Hide) Explanation/Reference
Remember, the source and destination MAC changes as each router hop along with the TTL being decremented but the source and destination IP address remain the same from source to destination.
I.146. Refer to the exhibit. Host A pings interface S0/0 on router 3. What is the TTL value for that ping?
- 252
- 253
- 254
- 255
Show (Hide) Explanation/Reference
From the CCNA ICND2 Exam book: "Routers decrement the TTL by 1 every time they forward a packet; if a router decrements the TTL to 0, it throws away the packet. This prevents packets from rotating forever." I want to make it clear that before the router forwards a packet, the TTL is still remain the same. For example, in the topology above, pings to S0/1 and S0/0 of Router 2 have the same TTL.
I.147. Which of the following describes the roles of devices in a WAN? (Choose three.)
- A CSU/DSU terminates a digital local loop.
- A modem terminates a digital local loop.
- A CSU/DSU terminates an analog local loop.
- A modem terminates an analog local loop.
- A router is commonly considered a DTE device.
- A router is commonly considered a DCE device.
Show (Hide) Explanation/Reference
The idea behind a WAN is to be able to connect two DTE networks together through a DCE network. The network's DCE device (includes CSU/DSU) provides clocking to the DTE-connected interface (the router's serial interface).
A modem modulates outgoing digital signals from a computer or other digital device to analog signals for a conventional copper twisted pair telephone line and demodulates the incoming analog signal and converts it to a digital signal for the digital device. A CSU/DSU is used between two digital lines -> A & D are correct but B & C are not correct.
For more explanation of answer D, in telephony thelocal loop (also referred to as a subscriber line) is the physical link or circuit that connects from the demarcation point of the customer premises to the edge of the carrier or telecommunications service provider's network. Therefore a modem terminates an analog local loop is correct.
I.148. The network administrator is asked to configure 113 point-to-point links. Which IP addressing scheme defines the address range and subnet mask that meet the requirement and waste the fewest subnet and host addresses?
- 10.10.0.0/16 subnetted with mask 255.255.255.252
- 10.10.0.0/18 subnetted with mask 255.255.255.252
- 10.10.1.0/24 subnetted with mask 255.255.255.252
- 10.10.0.0/23 subnetted with mask 255.255.255.252
- 10.10.1.0/25 subnetted with mask 255.255.255.252
Show (Hide) Explanation/Reference
We need 113 point-to-point links which equal to 113 sub-networks < 128 so we need to borrow 7 bits (because
2^7 = 128).
The network used for point-to-point connection should be /30.
So our initial network should be 30 ?7 = 23.
So 10.10.0.0/23 is the correct answer.
You can understand it more clearly when writing it in binary form:
/23 = 1111 1111.1111 1110.0000 0000
/30 = 1111 1111.1111 1111.1111 1100 (borrow 7 bits)
I.149. Which of the following IP addresses fall into the CIDR block of 115.64.4.0/22? (Choose three.)
- 115.64.8.32
- 115.64.7.64
- 115.64.6.255
- 115.64.3.255
- 115.64.5.128
- 115.64.12.128
I.150. Which of the following are types of flow control? (Choose three.)
- buffering
- cut-through
- windowing
- congestion avoidance
- load balancing
I.151. Which additional configuration step is necessary in order to connect to an access point that has SSID broadcasting disabled?
- Set the SSID value in the client software to public.
- Configure open authentication on the AP and the client.
- Set the SSID value on the client to the SSID configured on the AP.
- Configured MAC address filtering to permit the client to connect to the AP.
I.152. What is one reason that WPA encryption is preferred over WEP?
- A WPA key is longer and requires more special characters than the WEP key.
- The access point and the client are manually configured with different WPA key values.
- WPA key values remain the same until the client configuration is changed.
- The values of WPA keys can change dynamically while the system is used.
I.153. As a CCNA candidate, you must have a firm understanding of the IPv6 address structure. Refer to IPv6 address, could you tell me how many bits are included in each filed?
- 24
- 4
- 3
- 16
I.154. While troubleshooting a connectivity issue from a PC you obtain the following information:
What is the underlying cause of this problem?
- A remote physical layer problem exists.
- The host NIC is not functioning.
- TCP/IP has not been correctly installed on the host.
- A local physical layer problem exists.
I.155. Which name describes an IPV6 host-enable tunneling technique that uses IPV4 UDP,does not require dedicated gateway tunnels,and can pass through existing IPV4 NAT gateways?
- dual stack
- dynamic
- Teredo
- Manual 6to4
I.156. What are two advantages of Layer 2 Ethernet switches over hubs? (Choose two.)
- decreasing the number of collision domains
- filtering frames based on MAC addresses
- allowing simultaneous frame transmissions
- increasing the size of broadcast domains
- increasing the maximum length of UTP cabling between devices
I.157. What are two security appliances that can be installed in a network? (Choose two.)
- ATM
- IDS
- IOS
- IOX
- IPS
- SDM
I.158. A network administrator is planning a network installation for a large organization. The design requires 100 separate subnetworks, so the company has acquired a Class B network address. What subnet mask will provide the 100 subnetworks required, if 500 usable host addresses are required per subnet?
- 255.255.240.0
- 255.255.248.0
- 255.255.252.0
- 255.255.254.0
- 255.255.255.0
- 255.255.255.192
I.159. Which of the following services use UDP? (Choose three.)
- Telnet
- TFTP
- SNMP
- DNS
- SMTP
- HTTP
I.160. Which technology allows a large number of private IP addresses to be represented by a smaller number of public IP addresses?
- NAT
- NTP
- RFC 1631
- RFC 1918
I.161. What are three broadband wireless technologies? (Choose three)
- WiMax
- satellite Internet
- municipal Wi-Fi
- site-to-site VPN
- DSLAM
- CMTS
Show (Hide) Explanation/Reference
WiMAX is short for Worldwide Interoperability for Microwave Access. WiMAX is a family of wireless communication standards based on the IEEE 802.16 set of standards.
Satellite Internet provides Internet access via satellite. It is a form of wireless broadband technology. But it is usually slower than DSL and cable modem.
Municipal wireless network is a city-wide wireless network. This is usually done by providing municipal broadband via Wi-Fi to large parts or all of a municipal area by deploying a wireless mesh network. The typical deployment design uses hundreds of wireless access points deployed outdoors, often on poles.
DSLAM (Digital Subscriber Line Access Multiplexer) is a network device, usually at a telephone company central office, that receives signals from multiple customer Digital Subscriber Line (DSL) connections and puts the signals on a high-speed backbone line using multiplexing techniques. It is a cable technology, not a wireless technology.
Cable Modem Termination Systems (CMTS) is a piece of equipment, typically located in a cable company's headend or hubsite, which is used to provide high speed data services, such as cable Internet or Voice over Internet Protocol, to cable subscribers. It is a cable technology, not a wireless technology.
I.162. In which three ways is an IPv6 header simpler than an IPv4 header? (Choose three)
- Unlike IPv4 headers, IPv6 headers have a fixed length.
- IPv6 uses an extension header instead of the IPv4 Fragmentation field.
- IPv6 headers eliminate the IPv4 Checksum field.
- IPv6 headers use the Fragment Offset field in place of the IPv4 Fragmentation field.
- IPv6 headers use a smaller Option field size than IPv4 headers.
- IPv6 headers use a 4-bit TTL field, and IPv4 headers use an 8-bit TTL field.
Show (Hide) Explanation/Reference
The IPv4 and IPv6 headers are shown below for your comparison:
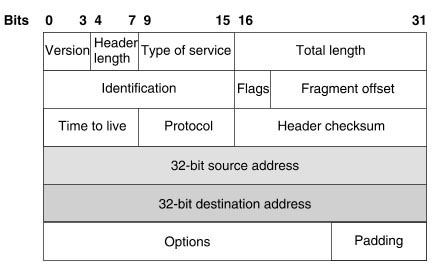
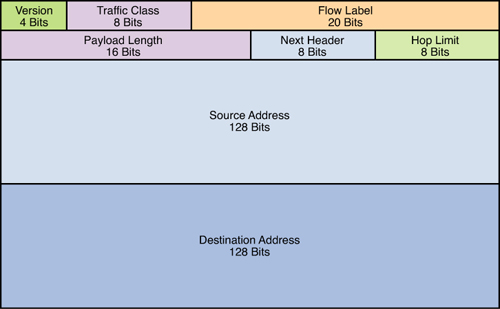
IPv6 Header fields
IPv6 eliminates the Header Checksum field, which handles error checking in IPv4. IPv6 depends on reliable transmission in the data link protocols and on error checking in upper-layer protocols instead -> Answer C is correct.
While IPv4 header's total length comprises a minimum of 20 octets (8 bits per octet), IPv6 header has only 8 fields with a fixed length of 40 octets -> Answer A is correct.
IPv4 header does not have a fixed length because of the Options fields. This field is used to convey additional information on the packet or on the way it should be processed. Routers, unless instructed otherwise, must process the Options in the IPv4 header. The processing of most header options pushes the packet into the slow path leading to a forwarding performance hit.
IPv4 Options perform a very important role in the IP protocol operation therefore the capability had to be preserved in IPv6. However, the impact of IPv4 Options on performance was taken into consideration in the development of IPv6. The functionality of Options is removed from the main header and implemented through a set of additional headers calledextension headers. The "Next Header" field in IPv6 can be used to point to the extension headers.
Reference: http://www.cisco.com/en/US/technologies/tk648/tk872/technologies_white_paper0900aecd8054d37d.html
I.163. Which type of address is the public IP address of a NAT device?
- outside public
- inside local
- inside global
- inside public
- outside global
- outside local
Show (Hide) Explanation/Reference
NAT use four types of addresses:
* Inside local address – The IP address assigned to a host on the inside network. The address is usually not an IP address assigned by the Internet Network Information Center (InterNIC) or service provider. This address is likely to be an RFC 1918 private address.
* Inside global address – A legitimate IP address assigned by the InterNIC or service provider that represents one or more inside local IP addresses to the outside world.
* Outside local address – The IP address of an outside host as it is known to the hosts on the inside network.
* Outside global address – The IP address assigned to a host on the outside network. The owner of the host assigns this address.

I.164. Which command can you enter to display the hits counter for NAT traffic?
- show ip nat statistics
- debug ip nat
- show ip debug nat
- clear ip nat statistics
Show (Hide) Explanation/Reference
An example of the output of the "show ip nat statistics" is shown below. As we can see, the "Hits" counter is displayed.
I.165. What is the first step in the NAT configuration process?
- Define inside and outside interfaces
- Define public and private IP addresses
- Define IP address pools
- Define global and local interfaces
Show (Hide) Explanation/Reference
In NAT configuration we should specify the inside and outside interfaces first with the command "ip nat inside" and "ip nat outside" under interface mode.
I.166. What is the best way to verify that a host has a path to other hosts in different networks?
- Ping the loopback address.
- Ping the default gateway.
- Ping the local interface address.
- Ping the remote network.
Show (Hide) Explanation/Reference
Ping is a tool that helps to verify IP-level connectivity; PathPing is a tool that detects packet loss over multiple-hop trips. When troubleshooting, the ping command is used to send an ICMP Echo Request to a target host name or IP address. Use Ping whenever you want to verify that a host computer can send IP packets to a destination host. You can also use the Ping tool to isolate network hardware problems and incompatible configurations.
If you call ipconfig /all and receive a response, there is no need to ping the loopback address and your own IP address — Ipconfig has already done so in order to generate the report. It is best to verify that a route exists between the local computer and a network host by first using ping and the IP address of the network host to which you want to connect. The command syntax is: ping < IP address > Perform the following steps when using Ping: Ping the loopback address to verify that TCP/IP is installed and configured correctly on the local computer. ping 127.0.0.1 If the loopback step fails, the IP stack is not responding. This might be because the TCP drivers are corrupted, the network adapter might not be working, or another service is interfering with IP. Ping the IP address of the local computer to verify that it was added to the network correctly.
Note that if the routing table is correct, this simply forwards the packet to the loopback address of 127.0.0.1. ping < IP address of local host > Ping the IP address of the default gateway to verify that the default gateway is functioning and that you can communicate with a local host on the local network. ping < IP address of default gateway > Ping the IP address of a remote host to verify that you can communicate through a router. ping < IP address of remote host > Ping the host name of a remote host to verify that you can resolve a remote host name. ping < Host name of remote host > Run a PathPing analysis to a remote host to verify that the routers on the way to the destination are operating correctly. pathping < IP address of remote host >
I.167. If host Z needs to send data through router R1 to a storage server, which destination MAC address does host Z use to transmit packets?
- the host Z MAC address
- the MAC address of the interface on R1 that connects to the storage server
- the MAC address of the interface on R1 that connects to host Z
- the MAC address of the storage server interface
Show (Hide) Explanation/Reference
Host Z will use ARP to get the MAC address of the interface on R1 that connects to it and use this MAC as the destination MAC address. It use the IP address of the storage server as the destination IP address.
For example in the topology below, host A will use the MAC address of E0 interface of the router as its destination MAC address to reach the Email Server.
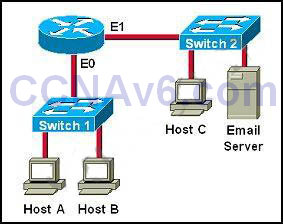
I.168. While you were troubleshooting a connection issue, a ping from one VLAN to another VLAN on the same switch failed. Which command verifies that IP routing is enabled on interfaces and the local VLANs are up?
- show ip interface brief
- show ip nat statistics
- show ip statistics
- show ip route
Show (Hide) Explanation/Reference
The "show ip nat statistics" only gives us information about NAT translation. We cannot know if IP routing is enabled or the VLANs are up not not.
The "show ip statistics" command does not exist.
In the Troubleshoot part of "How to configure InterVLAN Routing on Layer 3 switches" (http://www.cisco.com/c/en/us/support/docs/lan-switching/inter-vlan-routing/41860-howto-L3-intervlanrouting.html) Cisco recommends to use the "show ip interface brief" command as follows:
Also verify the interface VLAN status by issuing theshow ip interface brief command.
+ If the interface status is administratively down, enter the no shutdown command in the VLAN interface configuration mode.
+ If the interface status is down/down, verify the VTP configuration and that the VLANs have been added to the VLAN database. Check to see if a port is assigned to the VLAN and whether it is in the Spanning Tree forwarding state.
Initiate a ping from an end device in one VLAN to the interface VLAN on another VLAN in order to verify that the switch routes between VLANs. In this example, ping from VLAN 2 (10.1.2.1) to Interface VLAN 3 (10.1.3.1) or Interface VLAN 10 (10.1.10.1). If the ping fails, verify that IP routing is enabled and that the VLAN interfaces status is up with theshow ip interface brief command.
Also in the above link Cisco only mentions about the "show ip route" in the "Verify" part, not "Troubleshooting" part so "show ip interface brief" is a better answer.
I.169. Under which circumstance should a network administrator implement one-way NAT?
- when the network must route UDP traffic
- when traffic that originates outside the network must be routed to internal hosts
- when traffic that originates inside the network must be routed to internal hosts
- when the network has few public IP addresses and many private IP addresses require outside access
Show (Hide) Explanation/Reference
NAT operation is typically transparent to both the internal and external hosts. Typically, the internal host is aware of the true IP address and TCP or UDP port of the external host. Typically, the NAT device may function as the default gateway for the internal host. However, the external host is only aware of the public IP address for the NAT device and the particular port being used to communicate on behalf of a specific internal host.
NAT and TCP/UDP
"Pure NAT", operating on IP alone, may or may not correctly parse protocols that are totally concerned with IP information, such as ICMP, depending on whether the payload is interpreted by a host on the "inside" or "outside" of translation. As soon as the protocol stack is traversed, even with such basic protocols as TCP and UDP, the protocols will break unless NAT takes action beyond the network layer. IP packets have a checksum in each packet header, which provides error detection only for the header. IP datagrams may become fragmented and it is necessary for a NAT to reassemble these fragments to allow correct recalculation of higher-level checksums and correct tracking of which packets belong to which connection. The major transport layer protocols, TCP and UDP, have a checksum that covers all the data they carry, as well as the TCP/UDP header, plus a "pseudo-header" that contains the source and destination IP addresses of the packet carrying the TCP/UDP header. For an originating NAT to pass TCP or UDP successfully, it must recompute the TCP/ UDP header checksum based on the translated IP addresses, not the original ones, and put that checksum into the TCP/UDP header of the first packet of the fragmented set of packets. The receiving NAT must recompute the IP checksum on every packet it passes to the destination host, and also recognize and recompute the TCP/UDP header using the retranslated addresses and pseudo-header. This is not a completely solved problem. One solution is for the receiving NAT to reassemble the entire segment and then recompute a checksum calculated across all packets. The originating host may perform Maximum transmission unit (MTU) path discovery to determine the packet size that can be transmitted without fragmentation, and then set the don't fragment (DF) bit in the appropriate packet header field. Of course, this is only a one-way solution, because the responding host can send packets of any size, which may be fragmented before reaching the NAT.
I.170. When a router makes a routing decision for a packet that is received from one network and destined to another, which portion of the packet does if replace?
- Layer 2 frame header and trailer
- Layer 3 IP address
- Layer 5 session
- Layer 4 protocol
Show (Hide) Explanation/Reference
The Layer 2 information (source and destination MAC) would be changed when passing through each router. The Layer 3 information (source and destination IP addresses) remains unchanged.
I.171. On which type of device is every port in the same collision domain?
- a router
- a Layer 2 switch
- a hub
Show (Hide) Explanation/Reference
Collision domain A collision domain is, as the name implies, a part of a network where packet collisions can occur. A collision occurs when two devices send a packet at the same time on the shared network segment.
The packets collide and both devices must send the packets again, which reduces network efficiency.
Collisions are often in a hub environment, because each port on a hub is in the same collision domain. By contrast, each port on a bridge, a switch or a router is in a separate collision domain.
I.172. What is one requirement for interfaces to run IPv6?
- An IPv6 address must be configured on the interface.
- An IPv4 address must be configured.
- Stateless autoconfiguration must be enabled after enabling IPv6 on the interface.
- IPv6 must be enabled with the ipv6 enable command in global configuration mode.
Show (Hide) Explanation/Reference
To run IPv6 on an interface we have to configure an IPv6 on that interface somehow -> A is correct.
IPv6 must be enabled first but with the "ipv6 unicast-routing", not "ipv6 enable" command -> D is not correct.
I.173. Which destination IP address can a host use to send one message to multiple devices across different subnets?
- 172.20.1.0
- 127.0.0.1
- 192.168.0.119
- 239.255.0.1
Show (Hide) Explanation/Reference
In order to send traffic to multiple devices (not all) across different subnets we need to use multicast addresses, which are in the range 224.0.0.0 through 239.255.255.255 -> D is correct.
I.174. Which MTU size can cause a baby giant error?
- 1500
- 9216
- 1600
- 1518
Show (Hide) Explanation/Reference
Ethernet frame size refers to the whole Ethernet frame, including the header and the trailer while MTU size refers only to Ethernet payload. Baby giant frames refer to Ethernet frame size up to 1600 bytes, and jumbo frame refers to Ethernet frame size up to 9216 bytes (according to this link: http://www.cisco.com/c/en/us/support/docs/switches/catalyst-4000-series-switches/29805-175.html)
For example, standard Ethernet frame MTU is 1500 bytes. This does not include the Ethernet header and Cyclic Redundancy Check (CRC) trailer, which is 18 bytes in length, to make the total Ethernet frame size of 1518.
So according to strict definition, MTU size of 1600 cannot be classified as baby giant frames as the whole Ethernet frames will surely larger than 1600 -> Answer C is not correct.
Answer D is a better choice as the MTU is 1518, so the whole Ethernet frame would be 1536 (1518 + 18 Ethernet header and CRC trailer). This satisfies the requirement of baby giant frames "Baby giant frames refer to Ethernet frame size up to 1600 bytes".
I.175. DRAG DROP. Drag the terms on the left onto the appropriate OSI layer on the right. (Not all options are used.)
Select and Place:
Correct Answer:
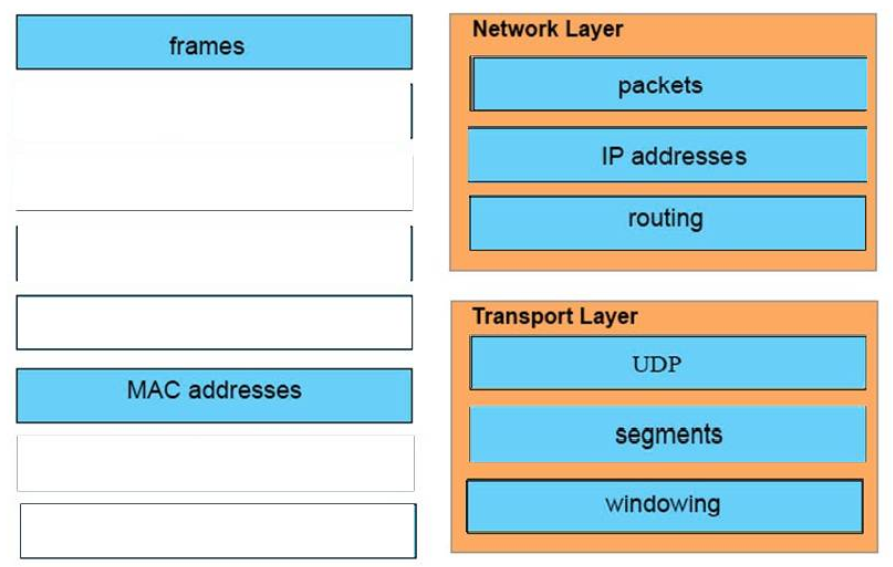
I.176. SIMULATION
A network associate is configuring a router for the Weaver company to provide internet access. The ISP has provided the company six public IP addresses of 198.18.184.105 – 198.18.184.110. The company has 14 hosts that need to access the internet simultaneously. The hosts in the company LAN have been assigned private space addresses in the range of 192.168.100.17 – 192.168.100.30.
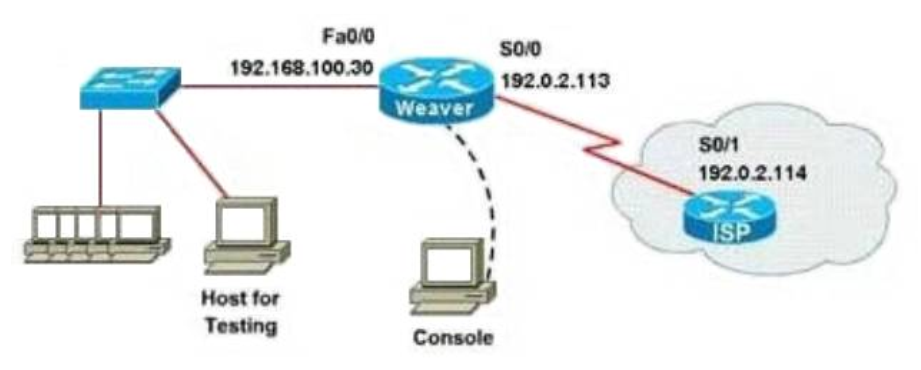
The following have already been configured on the router:
The basic router configuration
The appropriate interfaces have been configured for NAT inside and NAT outside
The appropriate static routes have also been configured (since the company will
be a stub network, no routing protocol will be required.)
All passwords have been temporarily set to "cisco"
The task is to complete the NAT configuration using all IP addresses assigned by the ISP to provide internet
access for the hosts in the weaver LAN. Functionality can be tested by clicking on the host provided for
testing.
Configuration information:
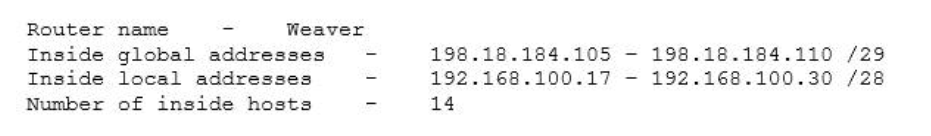
Correct Answer: See Explanation
Section: Network Fundamentals
Explanation
Explanation/Reference:
Explanation:
Step 1: Router Name
Step 2: NAT Configuration
Step 3: Save Configuration
Weaver#copy run start
Verification:
We can verify the answer by pinging the ISP IP Address (192.0.2.114) from Host for testing.
Click "Host for testing"
In command prompt, type "ping 192.0.2.114". If ping succeeded, then the NAT is working properly.
Screen Shots:
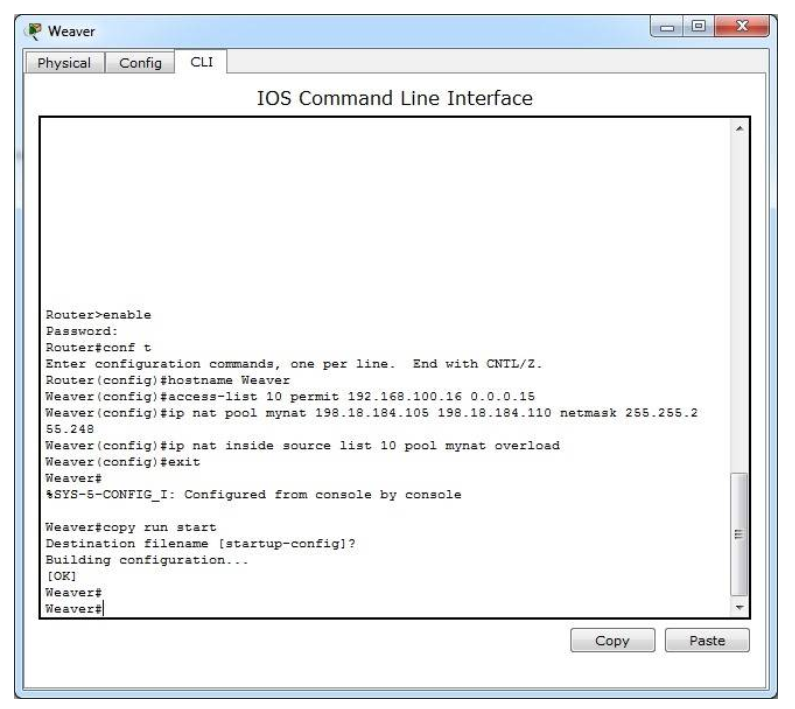
I.177. Instructions
This item contains several questions that you must answer. You can view these questions by clicking on the corresponding button to the left. Changing questions can be accomplished by clicking the numbers to the left question. In order to complete the questions, you will need to refer to the topology.
To gain access to the topology, click on the topology button of the screen. When you have finished viewing the topology, you can return to your questions by clicking on the Questions button to the left.
Each of the windows can be minimized by clicking on the [-]. You can also reposition a window by dragging it by the title bar.
Scenario
Refer to the topology. The diagram represents a small network with a single connection to the Internet.
If the router R1 has a packet with a destination address 192.168.1.255, what describes the operation of the network?
- R1 will forward the packet out all interfaces.
- R1 will drop this packet because this it is not a valid IP address.
- As R1 forwards the frame containing this packet, Sw-A will add 192.168.1.255 to its MAC table.
- R1 will encapsulate the packet in a frame with a destination MAC address of FF-FF-FF-FF-FF-FF.
- As R1 forwards the frame containing this packet, Sw-A will forward it to the device assigned the IP address of 192.168.1.255.
I.178. Instructions
This item contains several questions that you must answer. You can view these questions by clicking on the corresponding button to the left. Changing questions can be accomplished by clicking the numbers to the left question. In order to complete the questions, you will need to refer to the topology.
To gain access to the topology, click on the topology button of the screen. When you have finished viewing the topology, you can return to your questions by clicking on the Questions button to the left.
Each of the windows can be minimized by clicking on the [-]. You can also reposition a window by dragging it by the title bar.
Scenario
Refer to the topology. The diagram represents a small network with a single connection to the Internet.
Users on the 192.168.1.0/24 network must access files located on the Server 1. What route could be configured on router R1 for file requests to reach the server?
- ip route 0.0.0.0 0.0.0.0 s/0/0/0
- ip route 0.0.0.0 0.0.0.0 209.265.200.226
- ip route 209.165.200.0 255.255.255.0 192.168.1.250
- ip route 192.168.1.0 255.255.255.0 209.165.100.250
Show (Hide) Explanation/Reference
In order to allow the network of 192.168.1.0/24 to access Server 1, we need to establish a default route. The format of this default route is as follows:
ip route prefix mask {ip-address interface-type interface-number [ip-address]}
[distance] [name]
[permanent track number] [tag tag]
Based on the request of this subject, we need to configure the correct route as follows:
ip route 0.0.0.0 0.0.0.0 s0/0/0
I.179. Instructions
This item contains several questions that you must answer. You can view these questions by clicking on the corresponding button to the left. Changing questions can be accomplished by clicking the numbers to the left question. In order to complete the questions, you will need to refer to the topology.
To gain access to the topology, click on the topology button of the screen. When you have finished viewing the topology, you can return to your questions by clicking on the Questions button to the left.
Each of the windows can be minimized by clicking on the [-]. You can also reposition a window by dragging itby the title bar.
Scenario
Refer to the topology. The diagram represents a small network with a single connection to the Internet.
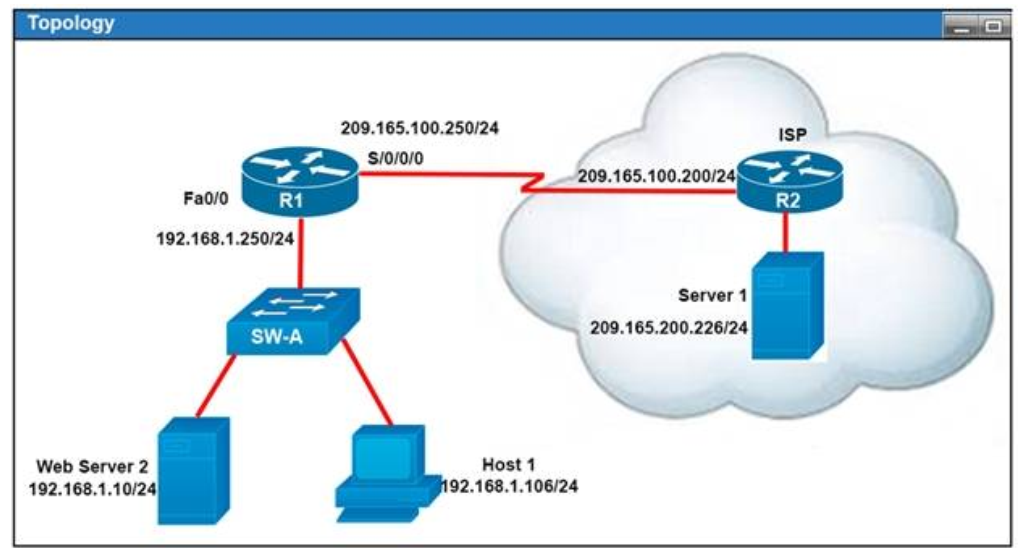
When a packet is sent from Host 1 to Server 1, in how many different frames will the packet be encapsulated as it is sent across the internetwork?
- 0
- 1
- 2
- 3
- 4
Show (Hide) Explanation/Reference
We believe the correct answer is 3 because the packet will be encapsulated in one more frame sent between
routers R1 and R2. Source MAC is interface S0/0/0 on router R1 and destination is
the serialinterface on router R2.
I.180. Instructions
This item contains several questions that you must answer. You can view these questions by clicking on the corresponding button to the left. Changing questions can be accomplished by clicking the numbers to the left question. In order to complete the questions, you will need to refer to the topology.
To gain access to the topology, click on the topology button of the screen. When you have finished viewing the topology, you can return to your questions by clicking on the Questions button to the left.Each of the windows can be minimized by clicking on the [-]. You can also reposition a window by dragging it by the title bar.
Scenario
Refer to the topology. The diagram represents a small network with a single connection to the Internet.
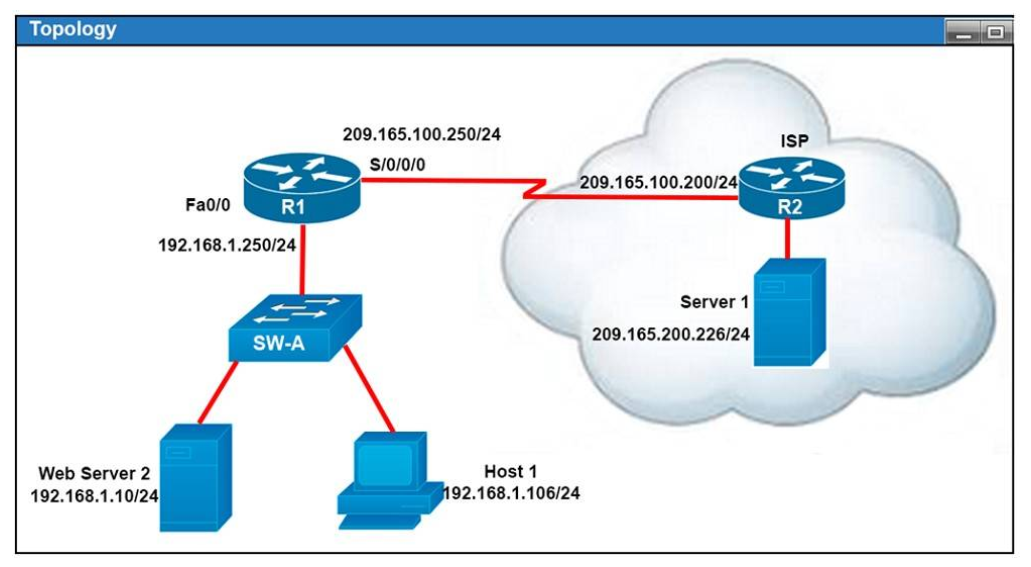
What must be configured on the network on order for users on the Internet to view web pages located on Web
Server 2?
-
- On Router R2, configure a default static route to the 192.168.1.0 network
- On router R2, configure DNS to resolve the URL assigned to Web Server 2 to the 192.168.1.10 address.
- On router R1, configure NAT to translate an address on the 209.165.100.0/24 network to 192.168.1.10.
- On router R1, configure DHCP to assign a registered IP address on the 209.165.100.0/24 network to Web
Server 2.
Show (Hide) Explanation/Reference
In order to allow internet users to access Web Server 2, we need to configure NAT address translation on
router R1.
I.181. Instructions
This item contains several questions that you must answer. You can view these questions by clicking on the corresponding button to the left. Changing questions can be accomplished by clicking the numbers to the left question. In order to complete the questions, you will need to refer to the topology.
To gain access to the topology, click on the topology button of the screen. When you have finished viewing the topology, you can return to your questions by clicking on the Questions button to the left.Each of the windows can be minimized by clicking on the [-]. You can also reposition a window by dragging it by the title bar.
Scenario
Refer to the topology. The diagram represents a small network with a single connection to the Internet.
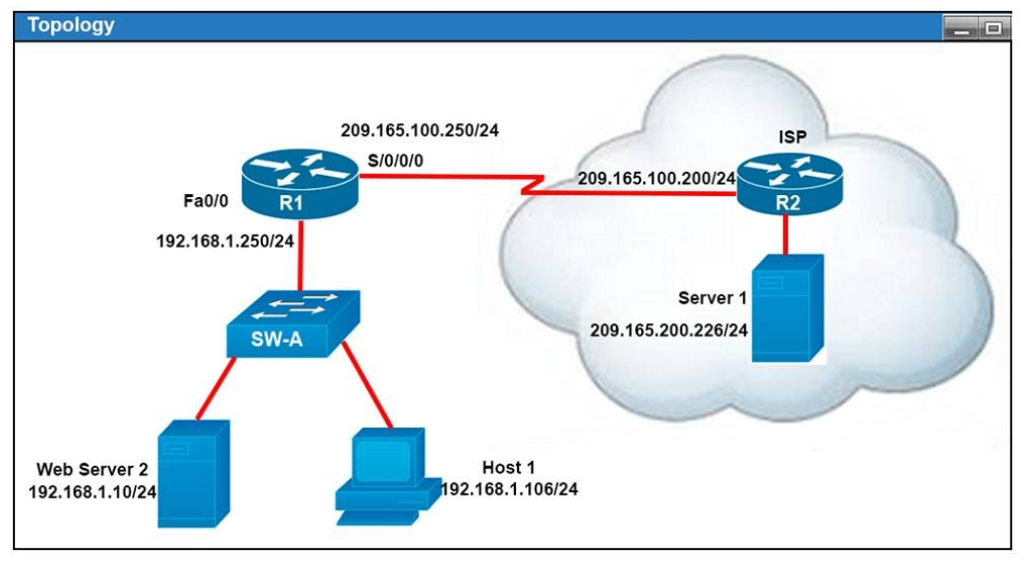
The router address 192.168.1.250 is the default gateway for both the Web Server 2 and Host 1. What is the correct subnet mask for this network?
- 255.255.255.0
- 255.255.255.192
- 255.255.255.250
- 255.255.255.252
Show (Hide) Explanation/Reference
1. Based on the information provided in the exhibit, we know that the IP address of the interface Fa0/0 is 192.168.1.250/24, that is to say the subnet mask is 255.255.255.0??
2. When configuring the correct IP address and not wasting IP address, the network of 192.168.1.0 needs to contain the following three IP addresses of interfaces:
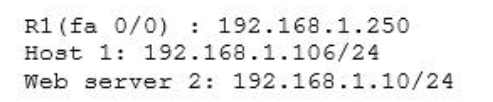
The correct mask is 255.255.255.0.
I.182. Which type of broadcast barely used in IPv4 which also exist in IPv6 like?
- unicast
- multicast
- broadcast
- anycast
I.183. Which type of cable must you use to connect to device with mdi interfaces?
- rolled
- crossover
- crossed
- straight through
I.184. DRAG DROP. Refer to the exhibit.
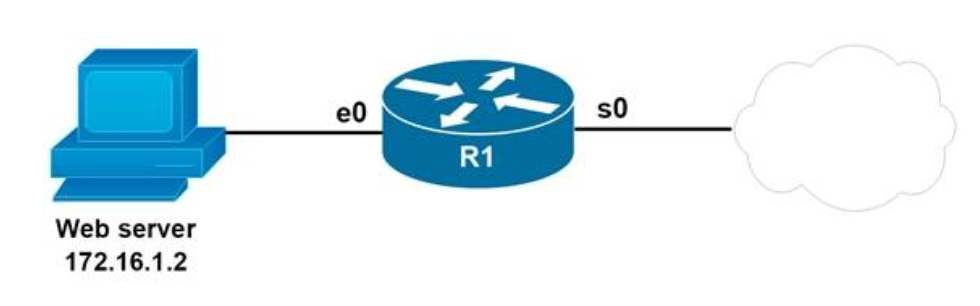
You are configuring the router to provide Static NAT for the web server.
Drag and drop the configuration commands from left onto the letters that correspond to its position in the
configuration on the right.
Select and Place:
Correct Answer:
I.185. DRAG DROP. Drag and drop each cable type from the left onto the type of connection for which it is best suited on the right.
Select and Place:
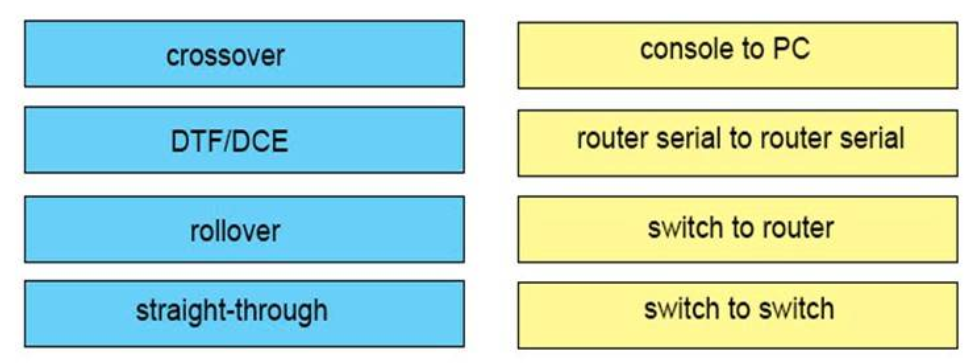
Correct Answer:
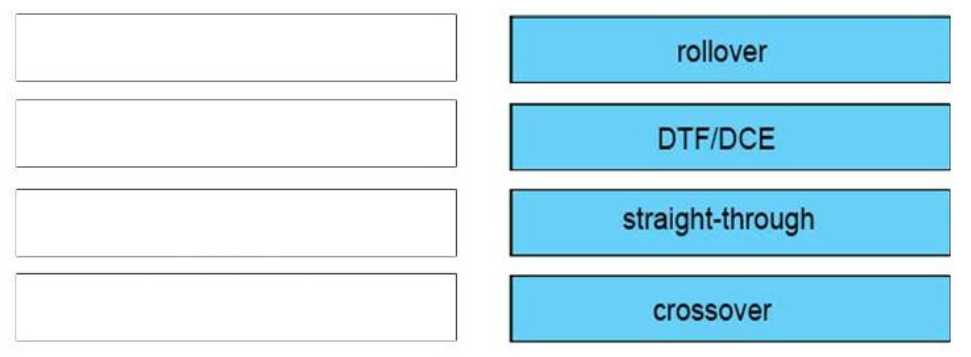
I.186. DRAG DROP. Drag and drop the characteristics of a cloud environment from the left onto the correct examples on the right
Select and Place:
Correct Answer:
I.187. DRAG DROP. Drag and drop each broadcast IP address on the left to the Broadcast Address column on the right. Not alloptions are used.
Select and Place:
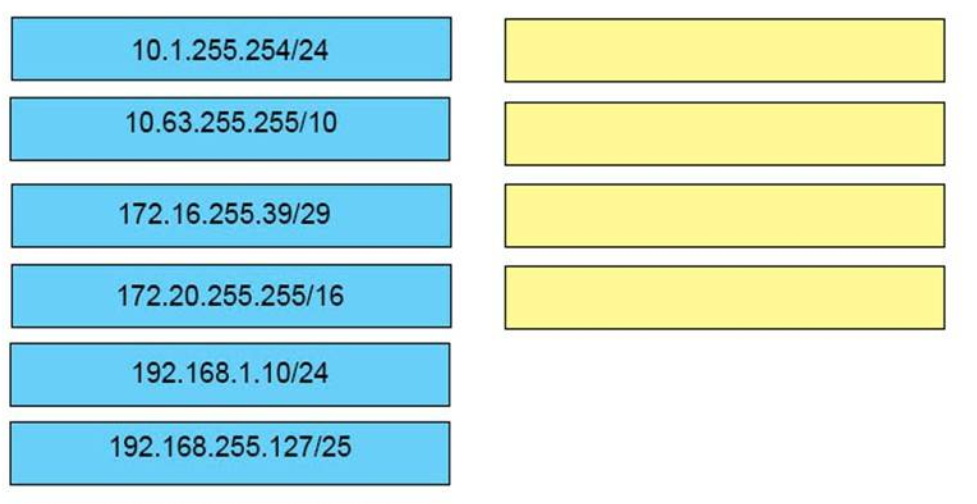
Correct Answer:
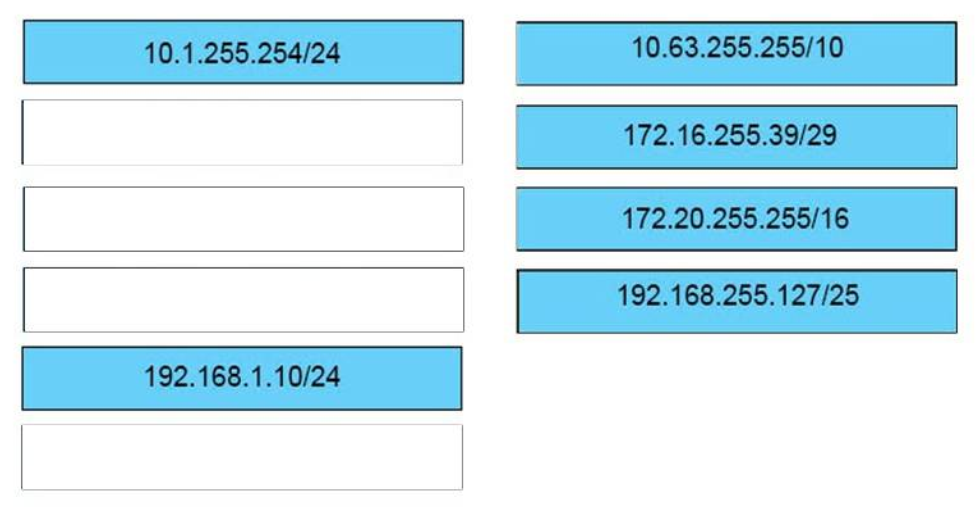
I.188. Which two of these statements are true of IPv6 address representation? (Choose two.)
- There are four types of IPv6 addresses: unicast, multicast, anycast, and broadcast.
- A single interface may be assigned multiple IPv6 addresses of any type.
- Every IPv6 interface contains at least one loopback address.
- The first 64 bits represent the dynamically created interface ID.
- Leading zeros in an IPv6 16 bit hexadecimal field are mandatory.
Show (Hide) Explanation/Reference
Leading zeros in IPv6 are optional do that 05C7 equals 5C7 and 0000 equals 0 -> D is not correct.
I.189. What is the first 24 bits in a MAC address called?
- NIC
- BIA
- OUI
- VAI
Show (Hide) Explanation/Reference
An Organizationally Unique Identifier (OUI) is a 24-bit number that uniquely identifies a vendor, manufacturer,
or other organization globally or worldwide. They are used as the first 24 nits of the MAC address to uniquely
identify a particular piece of equipment.
I.190. What is the difference between a CSU/DSU and a modem?
- A CSU/DSU converts analog signals from a router to a leased line; a modem converts analog signals from a router to a leased line.
- A CSU/DSU converts analog signals from a router to a phone line; a modem converts digital signals from a router to a leased line.
- A CSU/DSU converts digital signals from a router to a phone line; a modem converts analog signals from a router to a phone line.
- A CSU/DSU converts digital signals from a router to a leased line; a modem converts digital signals from a router to a phone line.
Show (Hide) Explanation/Reference
CSU/DSU is used to convert digital signals from a router to a network circuit such as a T1, while a modem is
used to convert digital signals over a regular POTS line.
I.191. Which two statements about EUI-64 addressing are true? (Choose two.)
- The address includes the hex digits FFFE after the last 24 bits of the interface MAC address.
- The address includes the hex digits FFFE after the first 24 bits of the interface MAC address
- A 64-bit interface identifier is derived from the interface MAC address.
- A locally administrated address has the universal/local bit set to 0.
- A 96-bit interface identifier is derived from the interface MAC address.
- The address includes the hex digits FFFE after the first 14 bits of the interface MAC address.
Show (Hide) Explanation/Reference
Extended Unique Identifier (EUI) allows a host to assign itself a unique 64-Bit IPv6 interface identifier (EUI-64). This feature is a key benefit over IPv4 as it eliminates the need of manual configuration or DHCP as in the world of IPv4. The IPv6 EUI-64 format address is obtained through the 48-bit MAC address. The MAC address is first separated into two 24-bits, with one being OUI (Organizationally Unique Identifier) and the other being NIC specific. The 16-bit 0xFFFE is then inserted between these two 24-bits for the 64-bit EUI address. IEEE has chosen FFFE as a reserved value which can only appear in EUI-64 generated from the an EUI-48 MAC address.
For example, suppose we have the MAC address of C601.420F.0007. It would be divided into two 24-bit parts, which are "C60142" (OUI) and "0F0007" (NIC). Then "FFFE" is inserted in the middle. Therefore we have the address: C601.42FF.FE0F.0007.
Then, according to the RFC 3513 we need to invert the Universal/Local bit ("U/L" bit) in the 7th position of the first octet. The "u" bit is set to 1 to indicate Universal, andit is set to zero (0) to indicate local scope.
Therefore with the subnet of 2001:DB8:0:1::/64, the full IPv6 address is 2001:DB8:0:1:C601:42FF:FE0F:7/64
I.192. DRAG DROP. Drag and Drop the descriptions of IP protocol transmissions from the left onto the correct IP traffic types on
the right.
Select and Place:
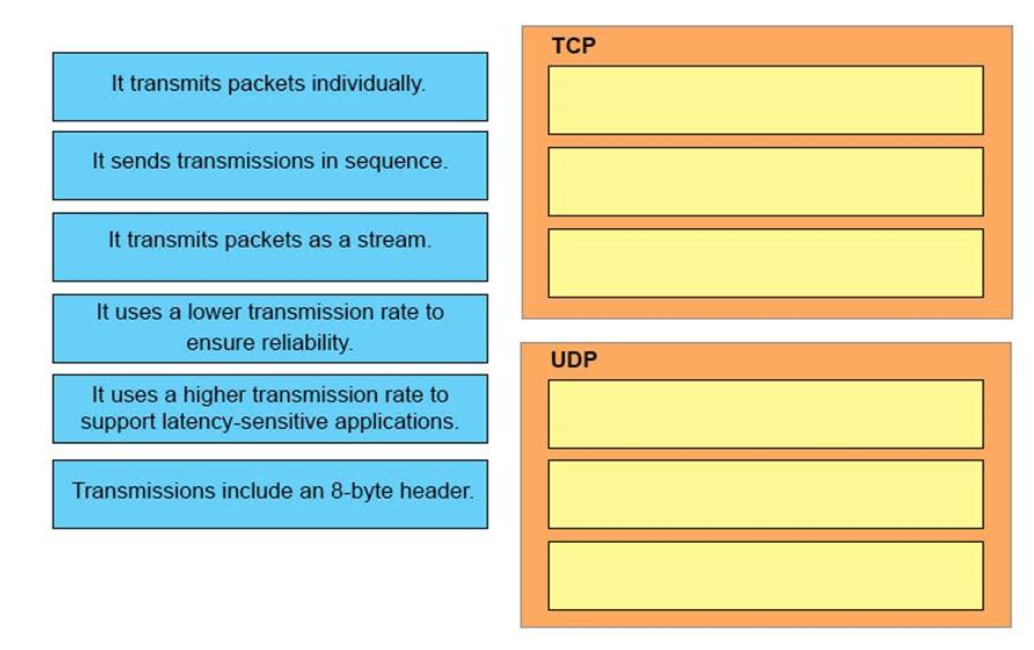
Correct Answer:
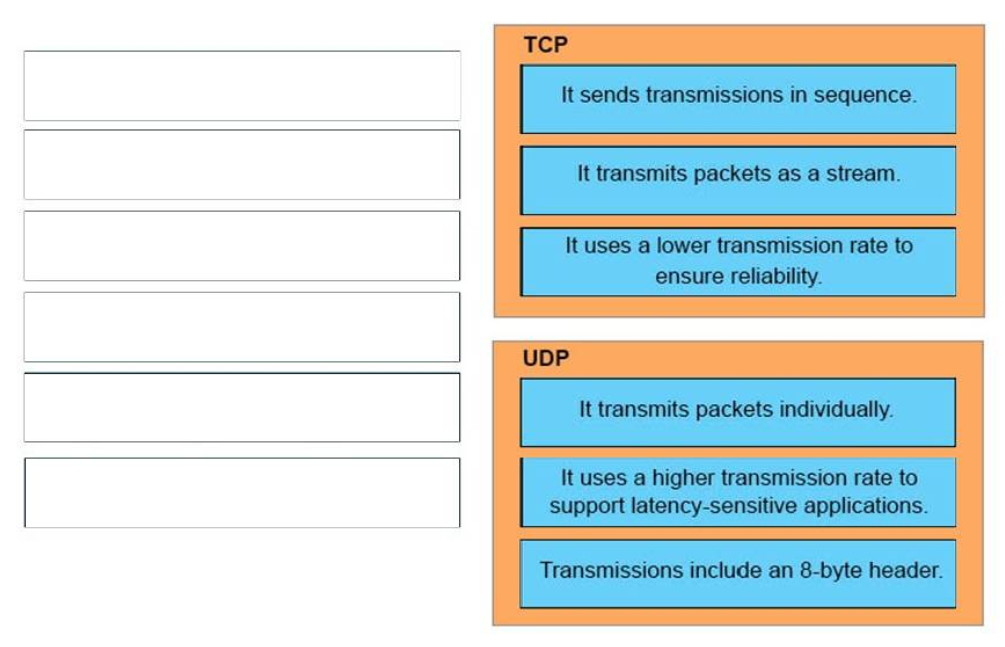
I.193. DRAG DROP. Drag each category on the left to its corresponding router output line on the right. Each router output line is in the result of a show ip interface command. Not all categories are used.
Select and Place:
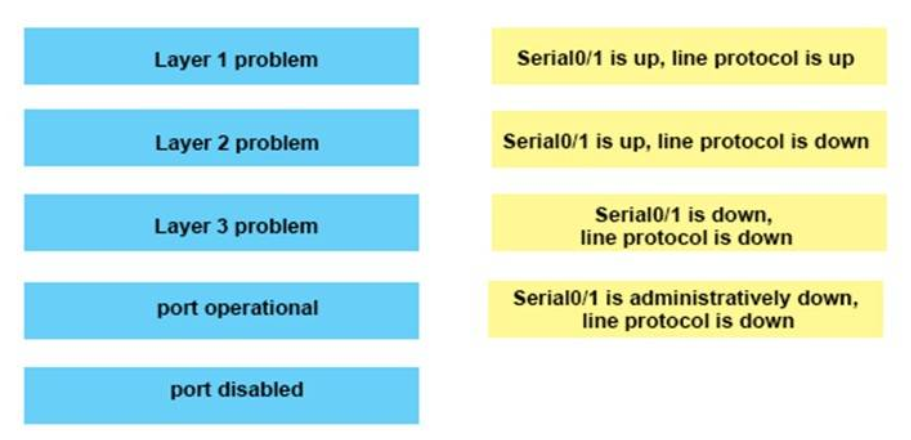
Correct Answer:
I.194. Which two statements about IPv4 multicast traffic are true? (Choose two.)
- It burdens the source host without affecting remote hosts.
- It uses a minimum amount of network bandwidth.
- It is bandwidth-intensive.
- It simultaneously delivers multiple streams of data.
- It is the most efficient way to deliver data to multiple receivers.
Show (Hide) Explanation/Reference
http://www.cisco.com/c/dam/en_us/about/ciscoitatwork/downloads/ciscoitatwork/pdf/cisco_it_case_study_multicast.pdf
Cisco IOS IP Multicast in the Cisco Network
"IP Multicast as defined in RFC1112, the standard for IP Multicast across networks and the Internet, supports one-to-many content needs by delivering application-source traffic to multiple users without burdening the source or the network, using a minimum amount of network bandwidth. At the point where paths diverge, Cisco routers replace IP Multicast packets in the network, resulting in the most efficient delivery of data to multiple receivers."
Even low-bandwidth applications can benefit fro IP Multicast when there are thousands of receivers. High-bandwidth applications, such as MPEG video, may need a large portion of the available network bandwidth for a single stream. In these applications, IP Multicast is the only way to efficiently send the same content to more than one receiver simultaneously, because it makes sure that only one copy of the data stream is sent across any one network link. It relies on each router in the stream to intelligently copy the data stream whenever it needs to deliver it to multiple receivers.
I.195. Which two statements about IPv6 router advertisement messages are true? (Choose two.)
- They use ICMPv6 type 134.
- The advertised prefix length must be 64 bits.
- The advertised prefix length must be 48 bits.
- They are sourced from the configured IPv6 interface address.
- Their destination is always the link-local address of the neighboring node.
Show (Hide) Explanation/Reference
IPv6 router advertisement message is one type of the ICMPv6 packets with Type field value of 134. It lists many facts, including the link-local IPv6 address of the router. Normally, it is sent to the all-IPv6-hosts local-scope multicast address of FF02::1. When sent in response to router solicitation messages (ICMPv6 Type 133), it flows back to either the unicast address of the host that sent the RS or to the all-IPv6-hosts address FF02::1.
The advertised IPv6 prefix length must be 64 bits for the stateless address autoconfiguration to be operational.
I.196. Which three technical services support cloud computing?
- network-monitored power sources
- layer 3 network routing
- ip localization
- redundant connections
- VPN connectivity
- extended SAN services
Show (Hide) Explanation/Reference
Four technical services are essential to supporting the high level of flexibility, resource availability, and transparent resource connectivity required for cloud computing:
+ The Layer 3 network offers the traditional routed interconnection between remote sites and provides end-user access to cloud services.
+ The extended LAN between two or more sites offers transparent transport and supports application and operating system mobility.
+ Extended SAN services support data access and accurate data replication.
+ IP Localization improves northbound and southbound traffic as well as server-to-server workflows.
Reference: https://www.cisco.com/c/en/us/products/collateral/ios-nx-os-software/ios-xr-software/white_paper_c11-694882.html
I.197. Which component of the Cisco SDN solution serves as the centralized management system?
- Cisco OpenDaylight
- Cisco ACI
- Cisco APIC
- Cisco IWAN
Show (Hide) Explanation/Reference
http://www.cisco.com/c/en/us/solutions/data-center-virtualization/application-centric-infrastructure/index.html
Cisco Application Policy Infrastructure Controller (APIC)
Provides single-click access to all Cisco ACI fabric information, enabling network automation, programmability, and centralized management.
http://www.cisco.com/c/en/us/products/cloud-systems-management/application-policy-infrastructure-controller-apic/index.html
The Cisco Application Policy Infrastructure Controller (Cisco APIC) is the unifying point of automation and management for the Application Centric Infrastructure (ACI) fabric. The Cisco APIC provides centralized access to all fabric information, optimizes the application lifecycle for scale and performance, and supports flexible application provisioning across physical and virtual resources.
The Cisco APIC provides centralized access to all fabric information, optimizes the application lifecycle for scale and performance, and supports flexible application provisioning across physical and virtual resources.
Centralized application-level policy engine for physical, virtual, and cloud infrastructures
Designed for automation, programmability, and centralized management, the Cisco APIC itself exposes northbound APIs through XML and JSON. It provides both a command-line interface (CLI) and GUI which utilize the APIs to manage the fabric holistically.
Cisco APIC provides:
A single pane of glass for application-centric network policies
Fabric image management and inventory
Application, tenant, and topology monitoring
Troubleshooting
I.198. What are the three major components of cisco network virtualization? (Choose Three)
- network access control
- path isolation
- virtual network services
- policy enforcement
Show (Hide) Explanation/Reference
Network virtualization architecture has three main components:
+ Network access control and segmentation of classes of users: Users are authenticated and either allowed or denied into a logical partition. Users a re segmented into employees, contractors and consultants, and guests, with respective access to IT assets. This component identifies users who are authorized to access the network and then places them into the appropriate logical partition.
+Path isolation: Network isolation is preserved across the entire enterprise: from the edge to the campus to the WAN and back again. This component maintains traffic partitioned over a routed infrastructure and transports traffic over and between isolated partitions. The function of mapping isolated paths to VLANs and to virtual services is also performed in component.
+Network Services virtualization: This component provides access to shared or dedicated network services such as security, quality of service (QoS), and address management (Dynamic Host Configuration Protocol [DHCP] and Domain Name System [DNS]). It also applies policy per partition and isolates application environments, if required.
Reference: http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-6500-series switches/white_paper_c11-531522.pdf
I.199. Which IPV6 function serves the same purpose as ARP entry verification on an IPv4 network?
- interface ip address verification
- MAC address table verification
- neighbor discovery verification
- Routing table entry verification
Show (Hide) Explanation/Reference
I.200. When you troubleshoot an IPv4 connectivity issue on a router, which three router configuration checks you must perform?
- Verify that the router interface IP address is correct.
- Verify that the DNS is configured correctly.
- Verify that the router and the host use the same subnet mask.
- Verify that the router firmware is up-to-date.
- Verify that a default route is configured.
- Verify that the route appears in the Routing table
I.201. Which Type of ipv6 unicast ip address is reachable across the internet?
- Unique Local
- Compatible
- Link local
- Global
I.202. Which two statements about IPv6 address 2002:ab10:beef::/48 are true?(choose two)
- The embedded IPv4 address can be globally routed.
- It is used for an ISATAP tunnel
- The embedded IPv4 address is an RFC 1918 address
- The MAC address 20:02:b0:10:be:ef is embedded into the IPv6 address
- It is used for a 6to4 tunnel
Show (Hide) Explanation/Reference
Any IPv6 address that begins with the 2002::/16 prefix is known as a 6to4 address. A 6to4 gateway adds its IPv4 address to this 2002::/16, creating a unique /48 prefix (because an IPv4 consists of 32 bits).
For example: In the IPv6 address 2002:ab10:beef::/48, "ab10:beef" is equivalent to 171.16.190.239 (convert "ab" in hexadecimal to "171" in decimal; "10" in hexadecimal to "16" in decimal…). Therefore the corresponding IPv4 address can be globally routed.
I.203. Which three functions are major components of a network virtualization architecture? (Choose three.)
- virtual network services
- policy enforcement
- network access control
- network resilienceE. authentication services
- path isolation
I.204. Which two benefits are provided by using a hierarchical addressing network addressing scheme? (Choose two.)
- reduces routing table entries
- auto-negotiation of media rates
- efficient utilization of MAC addresses
- dedicated communications between devices
- ease of management and troubleshooting
Show (Hide) Explanation/Reference
Here are some of the benefits of hierarchical addressing:
Reference: http://www.ciscopress.com/articles/article.asp?p=174107
I.205. Refer to the exhibit. Both switches are using a default configuration. Which two destination addresses will host 4 use to send data to host 1? (Choose two.)
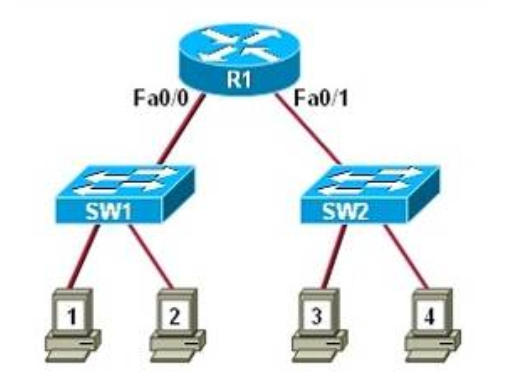
- the IP address of host 1
- the IP address of host 4
- the MAC address of host 1
- the MAC address of host 4
- the MAC address of the Fa0/0 interface of the R1 router
- the MAC address of the Fa0/1 interface of the R1 router
I.206. Which technology supports the stateless assignment of IPv6 addresses? (Choose two.)
- DNS
- DHCPv6
- DHCP
- autoconfiguration
Show (Hide) Explanation/Reference
DHCPv6 Technology Overview
IPv6 Internet Address Assignment Overview
IPv6 has been developed with Internet Address assignment dynamics in mind. Being aware that IPv6 Internet addresses are 128 bits in length and written in hexadecimals makes automation of address- assignment an important aspect within network design. These attributes make it inconvenient for a user to manually assign IPv6 addresses, as the format is not naturally intuitive to the human eye. To facilitate address assignment with little or no human intervention, several methods and technologies have been developed to automate the process of address and configuration parameter assignment to IPv6 hosts. The various IPv6 address assignment methods are as follows:
1. Manual Assignment
An IPv6 address can be statically configured by a human operator. However, manual assignment is quite
open to errors and operational overhead due to the 128 bit length and hexadecimal attributes of the addresses, although for router interfaces and static network elements and resources this can be an appropriate solution.
2. Stateless Address Autoconfiguration (RFC2462)
Stateless Address Autoconfiguration (SLAAC) is one of the most convenient methods to assign Internet
addresses to IPv6 nodes. This method does not require any human intervention at all from an IPv6 user. If one wants to use IPv6 SLAAC on an IPv6 node, it is important that this IPv6 node is connected to a network with at least one IPv6 router connected. This router is configured by the network administrator and sends out Router Advertisement announcements onto the link. These announcements can allow the on-link connected IPv6 nodes to configure themselves with IPv6 address and routing parameters, as specified in RFC2462, without further human intervention.
3. Stateful DHCPv6
The Dynamic Host Configuration Protocol for IPv6 (DHCPv6) has been standardized by the IETF through
RFC3315. DHCPv6 enables DHCP servers to pass configuration parameters, such as IPv6 network addresses, to IPv6 nodes. It offers the capability of automatic allocation of reusable network addresses and additional configuration flexibility. This protocol is a stateful counterpart to "IPv6 Stateless Address Autoconfiguration" (RFC 2462), and can be used separately, or in addition to the stateless autoconfiguration to obtain configuration parameters.
4. DHCPv6-PD
DHCPv6 Prefix Delegation (DHCPv6-PD) is an extension to DHCPv6, and is specified in RFC3633. Classical
DHCPv6 is typically focused upon parameter assignment from a DHCPv6 server to an IPv6 host running a DHCPv6 protocol stack. A practical example would be the stateful address assignment of "2001:db8::1" from a DHCPv6 server to a DHCPv6 client. DHCPv6-PD however is aimed at assigning complete subnets and other network and interface parameters from a DHCPv6-PD server to a DHCPv6-PD client. This means that instead of a single address assignment, DHCPv6-PD will assign a set of IPv6 "subnets". An example could be the assignment of "2001:db8::/60" from a DHCPv6-PD server to a DHCPv6-PD client. This will allow the DHCPv6-PD client (often a CPE device) to segment the received address IPv6 address space, and assign it dynamically to its IPv6 enabled interfaces.
5. Stateless DHCPv6
Stateless DHCPv6 is a combination of "stateless Address Autoconfiguration" and "Dynamic Host Configuration Protocol for IPv6" and is specified by RFC3736. When using stateless-DHCPv6, a device will use Stateless Address Auto-Configuration (SLAAC) to assign one or more IPv6 addresses to an interface, while it utilizes DHCPv6 to receive "additional parameters" which may not be available through SLAAC. For example, additional parameters could include information such as DNS or NTP server addresses, and are provided in a stateless manner by DHCPv6. Using stateless DHCPv6 means that the DHCPv6 server does not need to keep track of any state of assigned IPv6 addresses, and there is no need for state refreshment as result. On network media supporting a large number of hosts associated to a single DHCPv6 server, this could mean a significant reduction in DHCPv6 messages due to the reduced need for address state refreshments. From Cisco IOS 12.4(15)T onwards the client can also receive timing information, in addition to the "additional parameters" through DHCPv6. This timing information provides an indication to a host when it should refresh its DHCPv6 configuration data. This behavior (RFC4242) is particularly useful in unstable environments where changes are likely to occur.
I.207. Which command can you enter to verify that a 128-bit address is live and responding?
- traceroute
- telnet
- ping
- show ipv6
I.208. Which device allows users to connect to the network using a single or double radio?
- access point
- switch
- wireless controller
- firewall
Show (Hide) Explanation/Reference
Many Cisco access points offer single or double (dual) radio (2.4 and 5.0 GHz).
Note: The wireless controller automates wireless configuration and management functions. It does not connect directly to users.
I.209. A switch is configured with all ports assigned to VLAN 2 with full duplex FastEthernet to segment existing departmental traffic. What is the effect of adding switch ports to a new VLAN on the switch?
- More collision domains will be created.
- IP address utilization will be more efficient.
- More bandwidth will be required than was needed previously.
- An additional broadcast domain will be created.
I.210. When troubleshooting Ethernet connectivity issues, how can you verify that an IP address is known to a router?
- Check whether the IP address is in the routing table
- Check whether an ACL is blocking the IP address
- Check whether the IP address is in the CAM table
- Check whether the IP address is in the ARP table
Show (Hide) Explanation/Reference
If the IP address exists in the routing table then we can say the local router knew the way to reach that destination. But this question wants to ask if the destination has communicated to the local router or not ("an IP address is known to a router"). Maybe it is a tricky question.
I.211. Which two statements about the tunnel mode ipv6ip command are true? (Choose two.)
- It enables the transmission of IPv6 packets within the configured tunnel.
- It specifies IPv4 as the encapsulation protocol.
- It specifies IPv6 as the encapsulation protocol.
- It specifies IPv6 as the transport protocol.
- It specifies that the tunnel is a Teredo tunnel.
Show (Hide) Explanation/Reference
The "tunnel mode ipv6ip" command specifies IPv6 as the passenger protocol and IPv4 as both the encapsulation and transport protocol for the manual IPv6 tunnel. Notice that the tunnel source and destination are configured with IPv4 addressing and the tunnel interface is configured with IPv6.

An example of configuring using this command is shown below:
R1(config)#int tunnel 1 R1(config-if)#ipv6 address 1cde:7ea:348:1::3/127 R1(config-if)#tunnel source 10.1.1.1 R1(config-if)#tunnel destination 10.1.1.2 R1(config-if)#tunnel mode ipv6ip
I.212. Which configuration can you apply to enable encapsulation on a subinterface?
- interface FastEthernet 0/0
encapsulation dot1Q 30
ip address 10.1.1.30 255.255.255.0 - interface FastEthernet 0/0.30
ip address 10.1.1.30 255.255.255.0 - interface FastEthernet 0/0.30
description subinterface vlan 30 - interface FastEthernet 0/0.30
encapsulation dot1Q 30
ip address 10.1.1.30 255.255.255.0
Show (Hide) Explanation/Reference
To enabe encapsulation on a subinterface we have type the "encapsulation" command under that subinterface, not the main interface. An example of configuring encapsulation on subinterface of Fa0/1 is shown below:
Router(config)#interface f0/0 Router(config-if)#no shutdown (Note: The main interface f0/0 doesn't need an IP address but it must be turned on) Router(config)#interface f0/0.0 Router(config-subif)#encapsulation dot1q 10 Router(config-subif)#ip address 192.168.1.1 255.255.255.0 Router(config-subif)#interface f0/0.1 Router(config-subif)#encapsulation dot1q 20 Router(config-subif)#ip address 192.168.2.1 255.255.255.0
Note: In the "encapsulation dot1q 10", number 10 is the VLAN applied to that subinterface. Or you can understand that the subinterface belongs to that VLAN.
I.213. What happens when an 802.11a node broadcasts within the range of an 802.11g access point?
- The access point transmits, but the node is unable to receive.
- A connection occurs.
- Both the node and the access point are unable to transmit.
- The node transmits, but the access point is unable to receive.
Show (Hide) Explanation/Reference
802.11g is only compatible with 802.11b, not 802.11a so when 802.11a node broadcast, 802.11g access point cannot receive it.
I.214. A network administrator receives an error message while trying to configure the Ethernet interface of a router with IP address 10.24.24.24/29. Which statement explains the reason for this issue?
- This address is a broadcast address.
- VLSM-capable routing protocols must be enabled first on the router.
- The Ethernet interface is faulty.
- This address is a network address.
I.215. DRAG DROP. Drag and drop the networking features of functions from the left onto the planes on which they operate on the right.
Select and Place:
Correct Answer:
I.216. Which two statements about 1000BASE-T UTP cable are true? (Choose two.)
- It uses four wire pairs
- It is most appropriate for installations up to 1000 feet in length
- It is most appropriate for installations up to 1000 meters in length
- Both ends of the cable can transmit and receive simultaneously
- It uses four wires
I.217. Which two statements about IPv6 multicast addresses are true? (Choose two.)
- They use the prefix FC80::/8
- If the lifetime parameter is set to 1, the route is permanent
- They identify a group of interfaces on different devices
- They use the prefix FF00::/8
- If the scope parameter is set to 5, the route is local to the node
I.218. Which command can you enter on a Cisco IOS device to enable a scheduled algorithm that directs lookup calls to multiple DNS hosts?
- ip name-server 192.168.10.14 192.168.10.15
- ip domain list
- ip domain lookup
- ip domain round-robin
I.219. Which three elements are field in a basic Ethernet data frame? (Choose three.)
- Preamble
- Frame Check Sequence
- Header Checksum
- Length/Type
- Time to Live
- Version
I.220. Which prompt does a Cisco switch display when it is running in privileged exec mode?
- switch#
- switch(config)#
- switch(config-if)#
- switch>
I.221. Empty….
I.222. Which benefit of implementing a dual-homed WAN connection instead of a single-homed connection is true?
- Only dual-homed connections support recursive routing
- Only dual-homed connections enable an individual router to tolerate the loss of a network link
- Only dual-homed connections support split horizon with EIGRP
- Only dual-homed connections support OSPF in conjunction with BGP
Source: https://itexamanswers.net/cisco-ccna-200-125-exam-dumps-latest-new-questions-answers.html
Posted by: haileyhaileydelagrangee0272111.blogspot.com
Post a Comment for "70 410 Dumps Pdf Free Download"